Azure DevOps – Bulk IP Deal with Restriction Of Azure App Service Dynamically Utilizing PowerShell
This text is split into three components,
- Azure DevOps – Entry Restriction of Azure App Service utilizing Azure Administration Portal – We discovered how one can prohibit entry to the Azure App Service manually utilizing the Azure Portal.
- Azure DevOps – Bulk IP Deal with Restriction of Azure App Service dynamically utilizing PowerShell – We discovered how one can leverage PowerShell scripting to dynamically do bulk insertion of IP Addresses for configuring entry restrictions for the Azure App Service.
- Azure DevOps – Automate Bulk IP Deal with Restriction of Azure App Service dynamically utilizing PowerShell & Azure DevOps Pipeline – We’ll learn to automate the method of Entry Restriction each time there’s a change within the listing of IP addresses utilizing Azure DevOps Pipelines.
Conditions
- Azure Subscription
- Azure App Service
- PowerShell Core
- Azure PowerShell
- Visual Studio Code
Introduction
Within the Add Entry Restriction blade, you may present the next values to create a brand new Permit/Deny rule.
| Parameter | Description |
| Identify | The title of the rule. |
| Motion | Permit – deciding on this selection will let the consumer entry the App Service from the given IP Deal with (within the IP Deal with Block) Deny – deciding on this selection will NOT let the consumer entry the App Service from the given IP Deal with (within the IP Deal with Block) |
| Precedence | The precedence is given to this rule. |
| Kind | Choose IPV4 (extra on this under) |
| IP Deal with Block | Present the IP Deal with Vary. If you want to say just one IP Deal with then present one thing on this format 1.1.1.1/32 |
Once we did that, the foundations are created and saved contained in the ipSecurityRestrictions array of the Azure App Service Properties. We are able to evaluation these Properties utilizing the assets.azure.com web site as proven under,
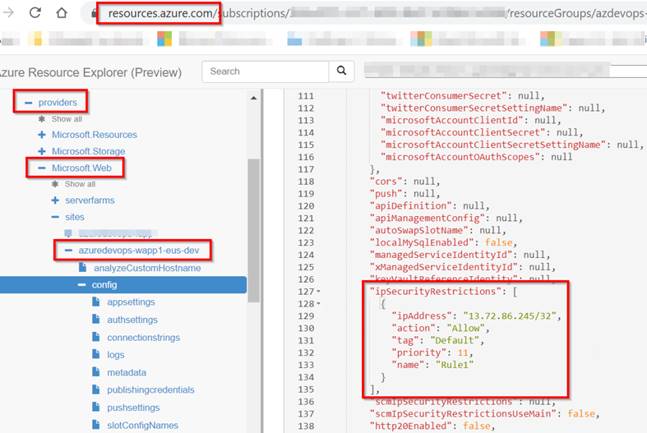
Azure DevOps – Bulk IP Deal with Restriction of Azure App Service dynamically utilizing PowerShell – Sources
If you want so as to add a number of IP Addresses in a single shot, then it’s preferable so as to add these a number of IP Addresses to this array.
On this article, we’re going to get the reference of those config properties, modify the ipSecurityRestrictions array and replace the App Service Properties.
Under is the logic that we’re going to implement on this article utilizing PowerShell.
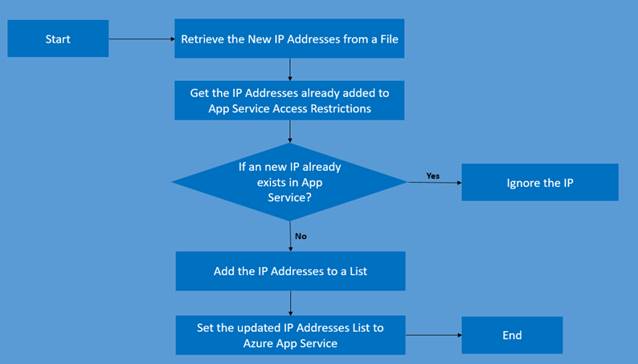
Azure DevOps – Bulk IP Deal with Restriction of Azure App Service dynamically utilizing PowerShell – Circulation Chart
Let’s create a brand new file that comprises all of the IP Addresses that we wish to Permit / Block. I’ve created a File named IPAddress.txt. It’s a Comma Separated file as proven under,
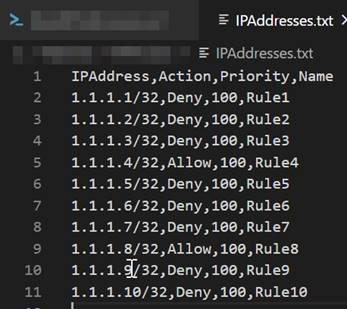
Azure DevOps – Bulk IP Deal with Restriction of Azure App Service dynamically utilizing PowerShell – IPAddresses File
Create a brand new PowerShell File named ReadIPAddress.ps1 utilizing Visual Studio Code utilizing the under code,
- Param(
- [Parameter(Mandatory = $true)]
- [string] $ResourceGroupName,
- [Parameter(Mandatory = $true)]
- [string] $WebAppName,
- [Parameter(Mandatory = $true)]
- [string] $IPAddressSourceFileName)
- #Step1 – Get All IP Addresses from the File
- $SourceIPAddresses = (Get – Content material$IPAddressSourceFileName).Trim() | ConvertFrom – Csv
- #Step2 – Get All current IP Addresses from the Config of App Service
- $APIVersion = ((Get – AzResourceProvider – ProviderNamespaceMicrosoft.Internet).ResourceTypes | The place – ObjectResourceTypeName – eqsites).ApiVersions[0]
- $config = (Get – AzResource – ResourceTypeMicrosoft.Internet / websites / config – Identify$WebAppName – ResourceGroupName$ResourceGroupName – ApiVersion$APIVersion)
- #Step3 – Put together the new IP Addresses listing from that IPAddressList file and acquire all the new ones into the $IpSecurityRestrictions assortment
- foreach($itemin$SourceIPAddresses) {
- $Rule = $config.Properties.ipSecurityRestrictions | The place – Object {
- $_.ipAddress – eq$merchandise.IPAddress
- }
- if ($null – ne$Rule) {
- Write – Host – ForegroundColorGreen ‘No Motion on the IP:’
- $merchandise.ipAddress
- } else {
- $config.Properties.ipSecurityRestrictions += $merchandise
- }
- }
- #Step4 – Lastly replace the new IP Addresses to Azure App Service
- Set – AzResource – ResourceId$config.ResourceId – Properties$config.Properties – ApiVersion$APIVersion – Pressure
As a way to run the above command from Visual Studio Code, navigate to the Terminate and run the under command,
- .ReadIPAddresses.ps1 azdevops-rg-eus-dev azuredevops-wapp1-eus-dev IPAddresses.txt
When you run the above command, you’d see the output as proven under,
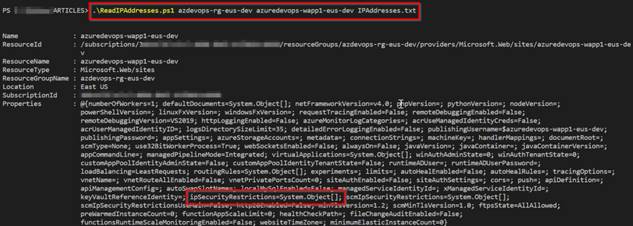
Azure DevOps – Bulk IP Deal with Restriction of Azure App Service dynamically utilizing PowerShell – Output
Lastly, all of the IP Addresses might be added to the Entry Restrictions blade as proven under,
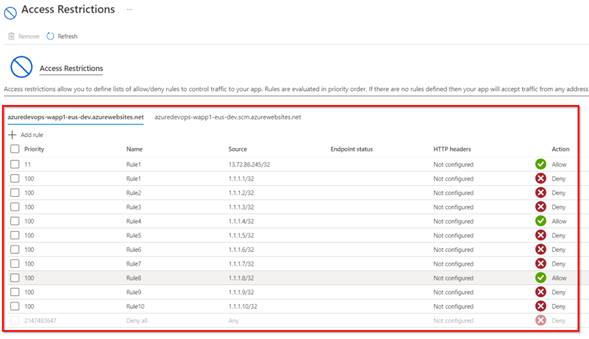
Azure DevOps – Bulk IP Deal with Restriction of Azure App Service dynamically utilizing PowerShell – Last Entry Restrictions
That’s it. We’ve discovered how one can add the foundations utilizing PowerShell out of your native machine. Within the subsequent article, we are going to learn to mechanically run this utilizing Azure DevOps pipelines.