How To Entry Azure Key Vault Secrets and techniques By Relaxation API Utilizing Postman
Introduction
Azure Key Vault service is used retailer cryptographic keys, certificates, and secrets and techniques. This text demonstrates the right way to entry a secret saved in Azure Key Vault via a REST API name utilizing Postman. Equally, from any utility you may name an http request to retrieve a secret’s worth.
The Strategy
First, we have to register our utility in Azure Lively Listing. Everytime you register an utility in Azure AD, an utility object is mapped to service precept.
Then we have to add that service precept into the entry insurance policies of the important thing vault. As soon as all of the setup carried out in Azure, we are going to go forward and request an entry token from Postman after which we are going to name key vault API to retrieve secrets and techniques utilizing entry token.
Register App in Azure Lively Listing
Whenever you register an utility in Azure AD, it principally describes the applying to Azure AD and what permissions the applying ought to have when it accesses companies throughout Azure.The applying can authenticate by way of the Microsoft Id platform. The Microsoft Id platform implements OAuth 2.Zero authorization that helps a third-party utility to entry web-hosted sources.
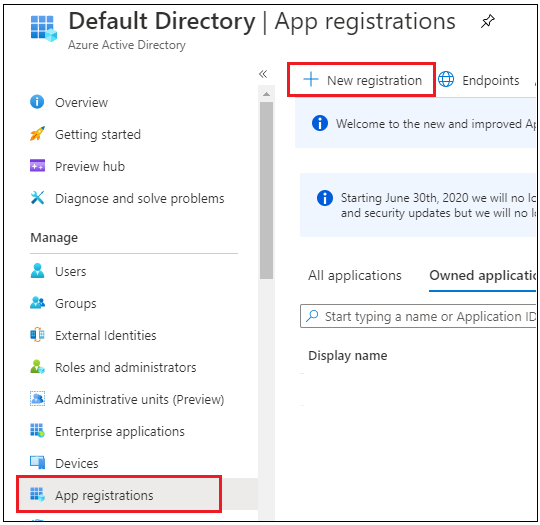
Go to Azure Lively Listing => App Registrations => New registration.
Present utility identify after which click on Register.
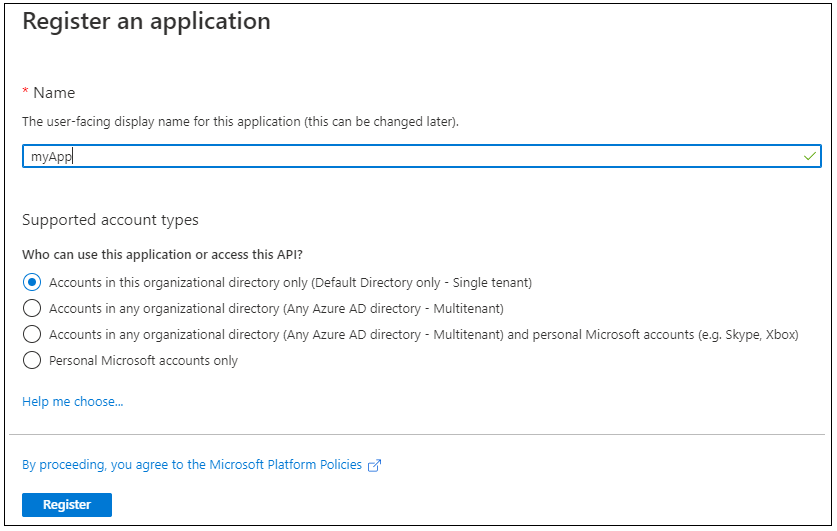
Now Click on on API permissions of the app that we simply added => Click on on Add a permission => Click on on Azure Key Vault and Choose. Then verify on permissions verify field and choose delegated permissions => Click on Add permission.
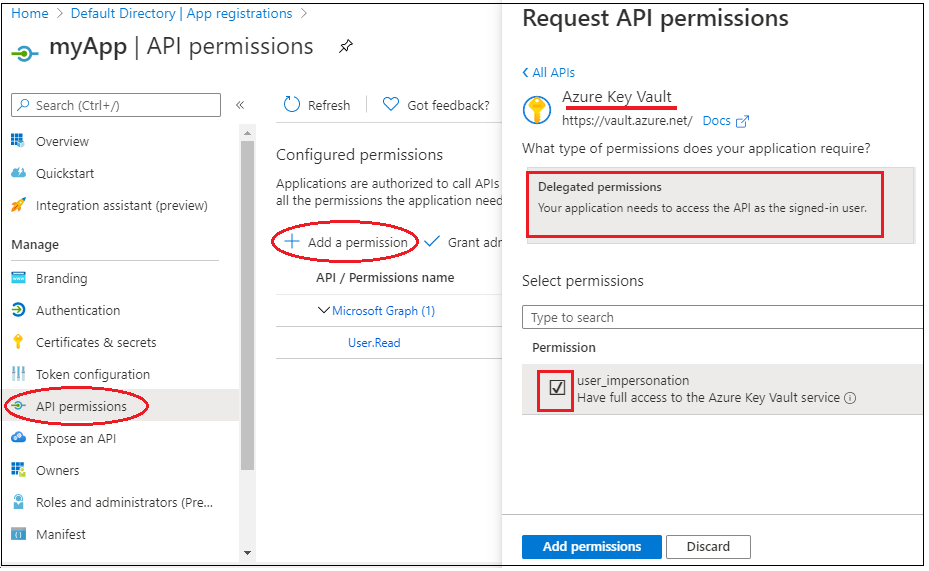
Now we have to generate consumer secret which might be required for authentication of calling utility. It principally acts like password. Let’s go forward and generate a brand new secret. Go to certificates and secrets and techniques part => click on on new consumer secret => Give identify to the consumer secret => Add.
Please observe that, oe you may solely copy the worth of your consumer secret one time. Copy the key worth and preserve it in a safe location. This worth might be required throughout relaxation name.
Add entry insurance policies to Key Vault
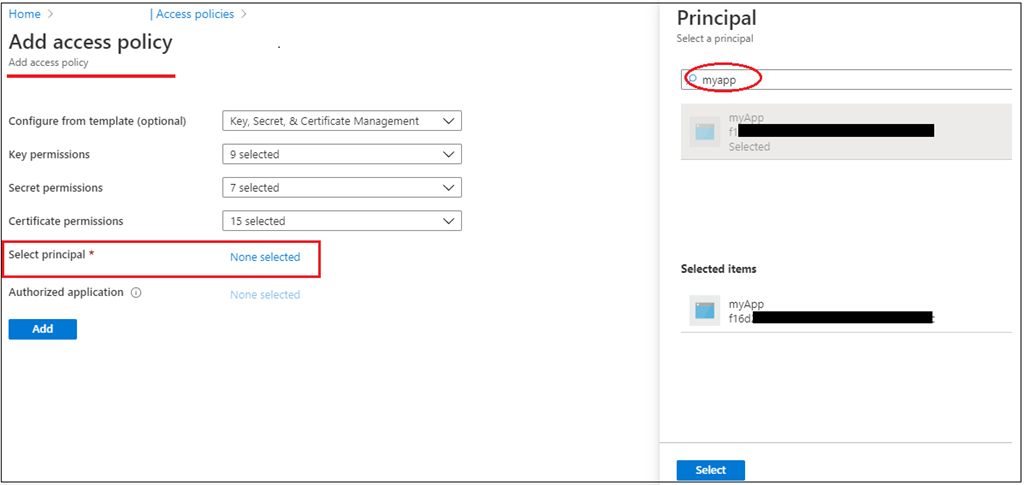
Now we’ve got to authorize the Azure AD app into key vault. To do that, go to Azure Key vault service => Choose the important thing vault => click on on “Entry Insurance policies” part of key vault after which click on on “+Add Entry Coverage” => Grant “get” permissions on Secret permission => Click on on search of choose precept and choose the Azure AD utility created earlier (in my case “myApp”) => Click on on Add and Save.
I created just a few secrets and techniques in key vaults with values which we are going to entry from Postman shortly.
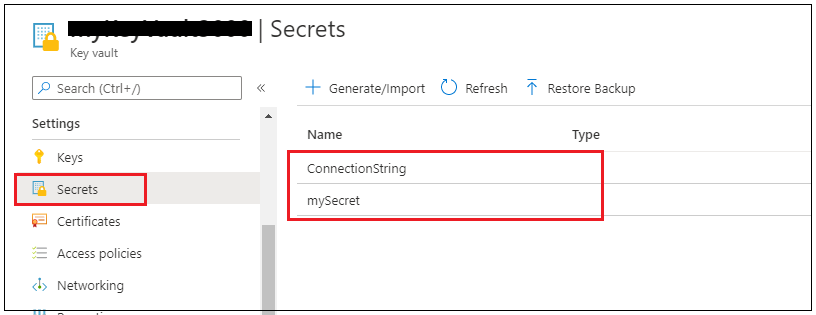
Now we’re able to entry these secrets and techniques from Postman.
Calling Key Vault API from Postman
To get key vault secrets and techniques from Postman, we’d like entry token. We are going to ship a POST request to get the token as under.
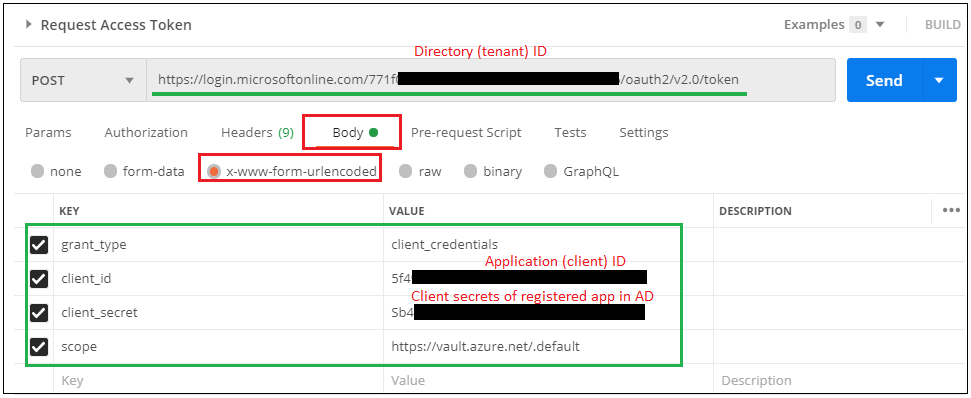
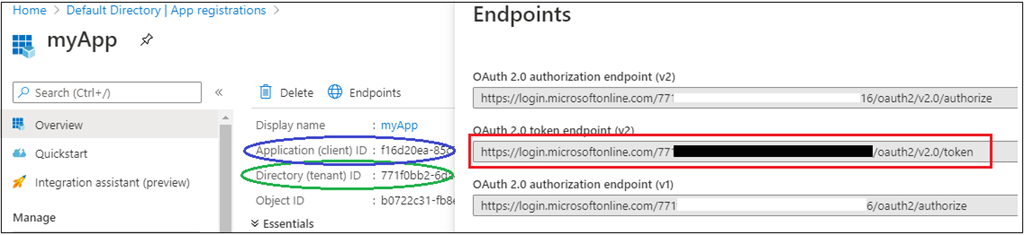
Right here, request url for entry token might be copied out of your registered app in Azure AD. In any other case you may copy under url and change {tenantID} worth with Listing ID of your registered app in Azure AD.
URL : POST https://login.microsoftonline.com/{tenantID}/oauth2/v2.0/token
These are the 4 keys that you need to point out right here in request physique whereas calling this endpoint.
- grant_type : client_credentials
- client_id : Copy Utility ID out of your registered app in Azure AD. Blue circle for under screenshot to your reference.
- client_secret : This might be Consumer secret worth of your registered app in Azure AD.
- scope : https://vault.azure.web/.default.
Now click on on Ship button to get entry token as response.
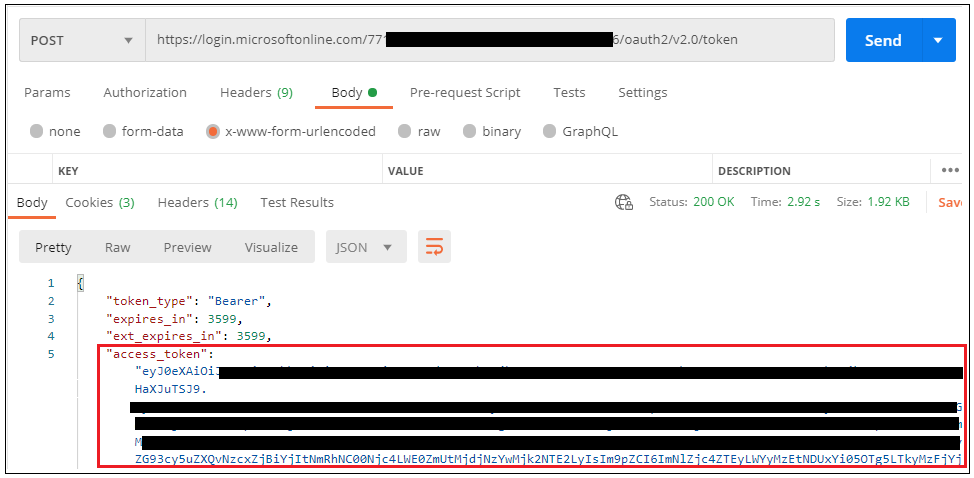
Superior! Now Create a brand new GET request in Postman to retrieve secret worth from Key Vault.
URL : GET https://keyvaultname.vault.azure.web/secrets and techniques/SecretName?api-version=2016-10-01
Right here, “keyvaultname” is the identify of your key vault and “SecretName” is the key that you simply need to entry.
Add Authorization key in header and worth might be bearer area and no matter is the entry token that you simply received from the earlier request e.g. “Bearer {entry token}”.
When you click on on Ship, you’ll get an analogous response as like under together with your secret worth.
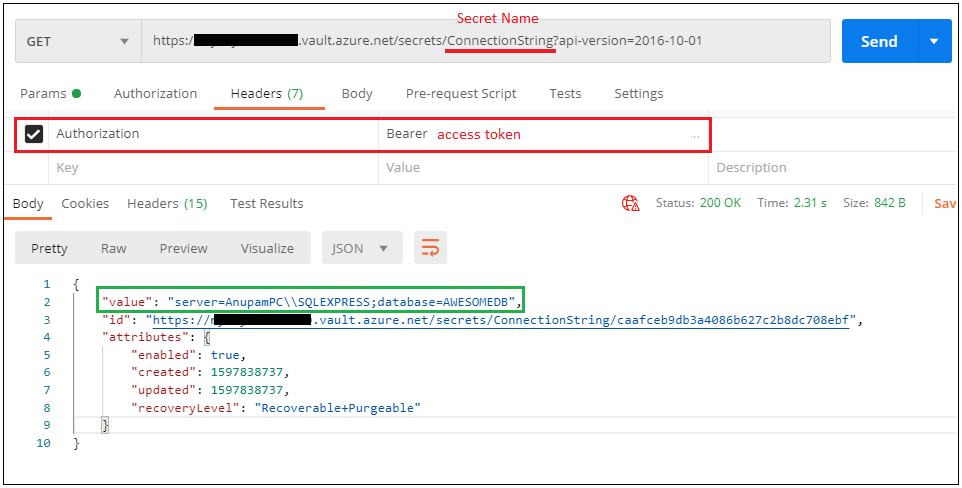
Wonderful! We’ve accessed Key Vault Secret by way of REST API from Postman.
Bear in mind, in the event you did not specify the bearer token within the request, you’ll get an error saying Unauthorized. So to be able to get info of key vault secrets and techniques, you need to be approved and that’s why we have to be certain that consumer utility (on this case postman) must be registered in Azure AD and corresponding service principal is a part of key vault entry insurance policies.
Conclusion
On this article, we’ve got created an app registration and in addition created a consumer secret for app registration. We’ve added key vault entry insurance policies. And eventually we referred to as Key Vault API from Postman utilizing entry token and efficiently retrieved the worth of a Key Vault Secret. Hope you discover this info helpful!