How To Validate Azure AD Token Utilizing Console Utility
On this article, you will notice methods to validate Azure AD token utilizing Console Utility.
Conditions
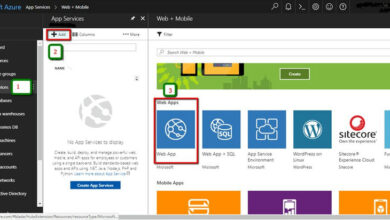
I’ve created an Azure App Service and I’ll log in to that software to get the entry token which might be validated.
Go to Developer Instruments -> Community and duplicate the entry token.
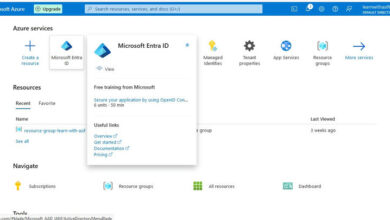
Navigate to Azure Portal (https://portal.azure.com) -> Azure Energetic Listing -> App Registrations -> Click on on the App registered.
Copy the tenant and software ID.
Within the left navigation, click on Certificates & Secrets and techniques. Create new consumer secret and duplicate the key.
Console Utility
Create a brand new console software utilizing Visual Studio 2019. Set up the next NuGet packages.
- Microsoft.IdentityModel.Protocols.OpenIdConnect
- System.IdentityModel.Tokens.Jwt
- Microsoft.Owin.Safety.Jwt
Copy and paste the next code. Replace the under variables together with your values (Copied from earlier steps).
- Token – entry token copied from developer software
- mySecret – App Secret Key
- myTenant – Tenant ID
- myAudience – Utility ID
- myIssuer – https://login.microsoftonline.com/<tenantID>/v2.0
- utilizing Microsoft.IdentityModel.Protocols;
- utilizing Microsoft.IdentityModel.Protocols.OpenIdConnect;
- utilizing Microsoft.IdentityModel.Tokens;
- utilizing System;
- utilizing System.Collections.Generic;
- utilizing System.Configuration;
- utilizing System.Globalization;
- utilizing System.IdentityModel.Tokens.Jwt;
- utilizing System.Linq;
- utilizing System.Linq.Expressions;
- utilizing System.Textual content;
- utilizing System.Threading.Duties;
- namespace AzureADTokenValidation
- {
- class Program
- {
- static async Job Major(string[] args)
- {
- string token = “eyJ0eXAiOiJKV1QiLCJhbGciOiJSUzI1NiIsImtpZCI6IkN0VHVoTUptRDVNN0RMZHpEMnYyeDNRS1NSWSJ9.eyJhdWQiOiI3YjFjZTFhZC1hZjE1LTRlNWYtOWFlNC1hYWYwYTY4YTdhYjQiLCJpc3MiOiJodHRwczovL2xvZ2luLm1pY3Jvc29mdG9ubGluZS5jb20vZThlNmQwMTgtYTgzNC00MDZiLTlmNDMtMmU5NGFlNDI1ODc2L3YyLjAiLCJpYXQiOjE1ODkyODQ2OTEsIm5iZiI6MTU4OTI4NDY5MSwiZXhwIjoxNTg5Mjg4NTkxLCJhaW8iOiJBVVFBdS84UEFBQUEyNWpRNzJBc3IyWHBYMEJlUkZRNU1lTTdSLy8zbnpIbUxDUHNYekJYRWZpSGlkQWM4Y0RPNHJoUUVEdk56OWtnRTdPK1pYbmxNTTVRNmk4RjZYY0hLZz09IiwibmFtZSI6IlZpamFpIEFuYW5kIFJhbWFsaW5nYW0iLCJub25jZSI6IjY1OWM5MjU0LTQyN2YtNDg5MC05ODQ5LTU0ZTk1Yjc0NDYyNCIsIm9pZCI6ImU2YmFkYTg2LTk4NDktNGFhNC1hZWQ0LTg5YzZlZmE5YTc0MSIsInByZWZlcnJlZF91c2VybmFtZSI6InZpamFpYW5hbmRAQzk4Ni5vbm1pY3Jvc29mdC5jb20iLCJzdWIiOiJIdjhtQ3RDVkx1NW8wYklrSDJVd2RCTnVUWTlqeC1RNUU4LTVuYU5pdkFJIiwidGlkIjoiZThlNmQwMTgtYTgzNC00MDZiLTlmNDMtMmU5NGFlNDI1ODc2IiwidXRpIjoiVml0alZEcVh5RS0yaWNLQUlRT19BQSIsInZlciI6IjIuMCJ9.UAT3FkgCBYqM7Mfux1V-yF1QTqg0Dlz4Y2G8VQqNqg3WXWdQWf8v4MHcrZVzycV6FSA0-C4ANRpkBxeX1mdmtic4l6e5onOsRS3r_PsWpp7mew_XlTt9TQ1W1pO5dn6lw6J4U3k41kmXVAPwH9hbZNEmVVM6KjNQLW-SdCfaJJIB0XVIqEK2HOlBPxSI8hugh9S5yRMYz6-xi7SrG-wQJtsa9s7Wz5O4FYW2YmjHdUIdj_xwJbfS6_rknJetO756okz4tHY70N3GAKlr_zvfXvuAMjXfsXQNQN5-TQnDcWVkvK6SrhCGQunlPmjvvTvJyp7KLZVrRhxnz8w98yaEfA”;
- string myTenant = “e8e6d018-a834-406b-9f43-2e94ae425876”;
- var myAudience = “7b1ce1ad-af15-4e5f-9ae4-aaf0a68a7ab4”;
- var myIssuer = String.Format(CultureInfo.InvariantCulture, “https://login.microsoftonline.com/{0}/v2.0”, myTenant);
- var mySecret = “t.GDqjoBYBhB.tRC@lbq1GdslFjk8=57”;
- var mySecurityKey = new SymmetricSecurityKey(Encoding.ASCII.GetBytes(mySecret));
- var stsDiscoveryEndpoint = String.Format(CultureInfo.InvariantCulture, “https://login.microsoftonline.com/{0}/.well-known/openid-configuration”, myTenant);
- var configManager = new ConfigurationManager<OpenIdConnectConfiguration>(stsDiscoveryEndpoint, new OpenIdConnectConfigurationRetriever());
- var config = await configManager.GetConfigurationAsync();
- var tokenHandler = new JwtSecurityTokenHandler();
- var validationParameters = new TokenValidationParameters
- {
- ValidAudience = myAudience,
- ValidIssuer = myIssuer,
- IssuerSigningKeys = config.SigningKeys,
- ValidateLifetime = false,
- IssuerSigningKey = mySecurityKey
- };
- var validatedToken = (SecurityToken)new JwtSecurityToken();
- tokenHandler.ValidateToken(token, validationParameters, out validatedToken);
- Console.WriteLine(validatedToken);
- Console.ReadLine();
- }
- }
- }
Construct and Check the answer
Hit F5. Azure AD token is validated and the validated token is displayed as proven under.
Abstract
Thus, on this article, you noticed methods to validate Azure AD token utilizing Console Utility.