Distinction Between Azure AD Roles And Position-Primarily based Entry Management (RBAC)
Introduction
Typically, we could have confusion between two phrases – Azure AD roles and Azure roles i.e. role-based entry management in Azure. On this article, I’ll clarify a few of the core differentiation between these two phrases.
What are Azure AD Roles?
Azure AD is nothing however an identification retailer in Azure. Right here we are able to outline customers, teams, purposes, and repair ideas. These customers can authenticate onto Azure and so they can entry sources which can be a part of Azure subscription.
We are able to assign Azure AD roles to a person and these permissions are usually given to handle the assorted facets of Azure AD.
Let’s say we need to give a person the power to register purposes in Azure, then we are able to assign them as utility administrator function or as an example we need to give the power for a person to handle teams, then we are able to assign the group’s administrator function to the person.
What’s Position-Primarily based Entry Management?
However, role-based entry management (RBAC) is supposed to authorize a person to make use of sources in Azure.
So for instance, you could possibly give a task for a person to go forward and provides them the power to create a storage account or to handle useful resource teams.
Position-based entry management could be given on the administration group degree, subscription degree, useful resource group degree, or on the useful resource degree.
RBAC has three fundamental roles that apply to all useful resource sorts:
- Proprietor
This function has full entry to all of the sources and might delegate entry to others. - Contributor
This function can create and handle all kinds of sources, however can’t grant entry to different customers and teams. - Reader
This function can view current Azure sources.
Assigning Azure AD Roles
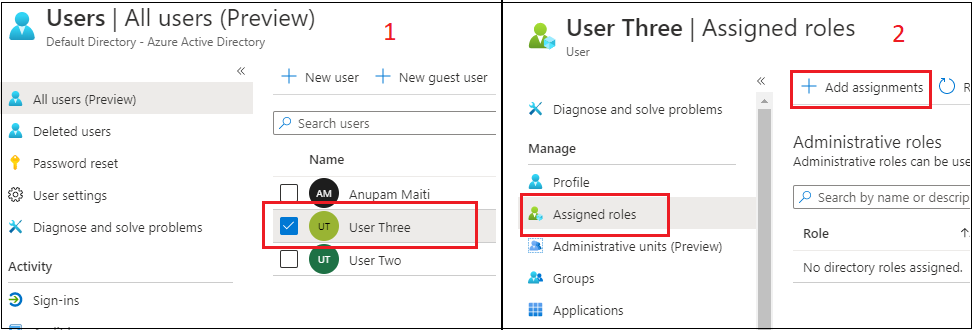
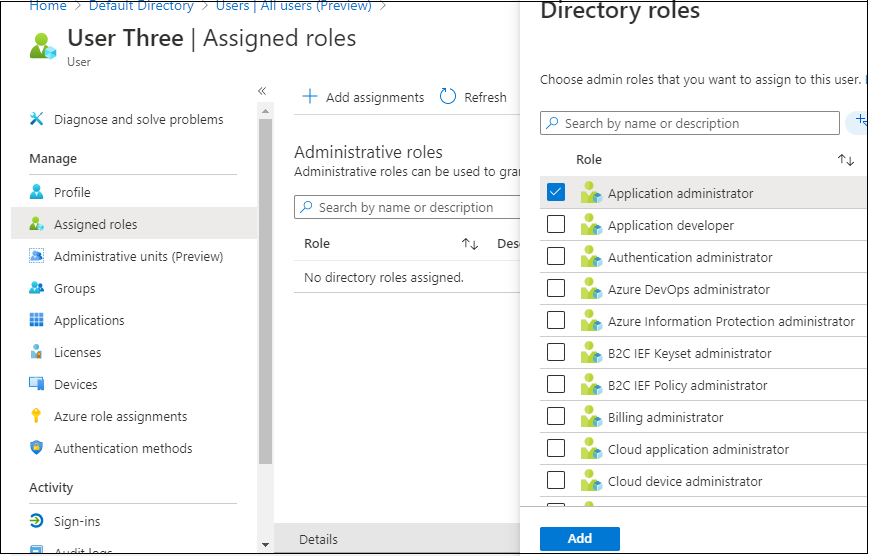
Go to Azure Lively Listing, and go to the Customers part => click on on a person for whom you need to add an AD Position. Now we are able to Assign roles for the person => Click on on Assigned Position => + Add assignments.
Now you will notice a listing of obtainable Azure AD roles. You may choose any function and click on on the Add button.
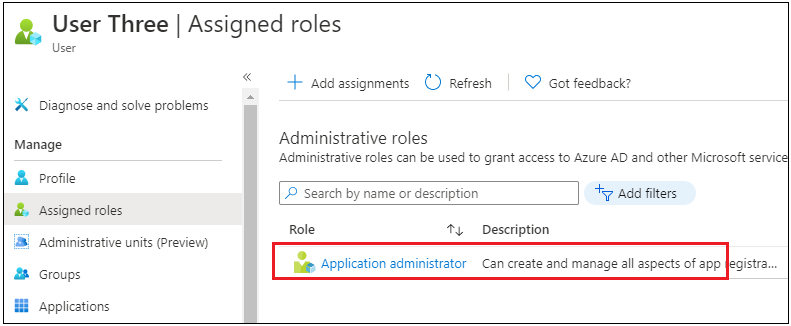
You’ll then see the function assigned to the person.
Assigning Position-Primarily based Entry Management
As we all know, RBAC is used to present entry to sources in Azure. For example you need to give RBAC entry to a person for Useful resource Group.
Go to go Useful resource Group and click on on the Entry Management (IAM) choice
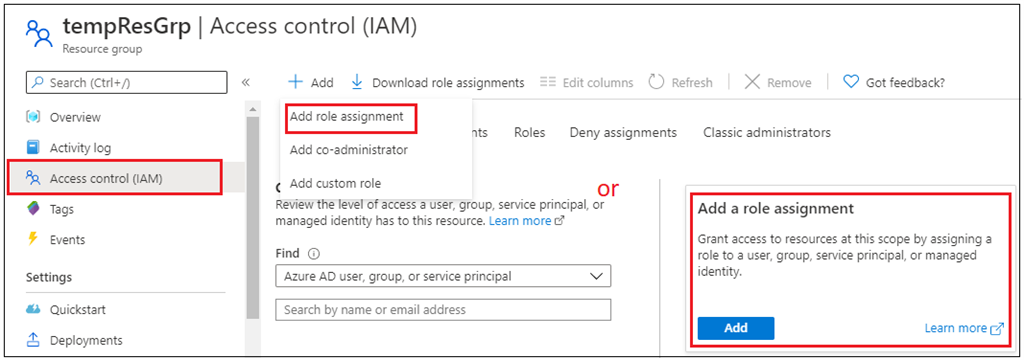
Now click on on the Add function task. Within the subsequent display screen, you need to select the Position to assign, and the principal to assign it to.
First, you possibly can select a Position, then select entry assign to, the final seek for the person, and choose. As soon as the person is chosen, click on on Save.
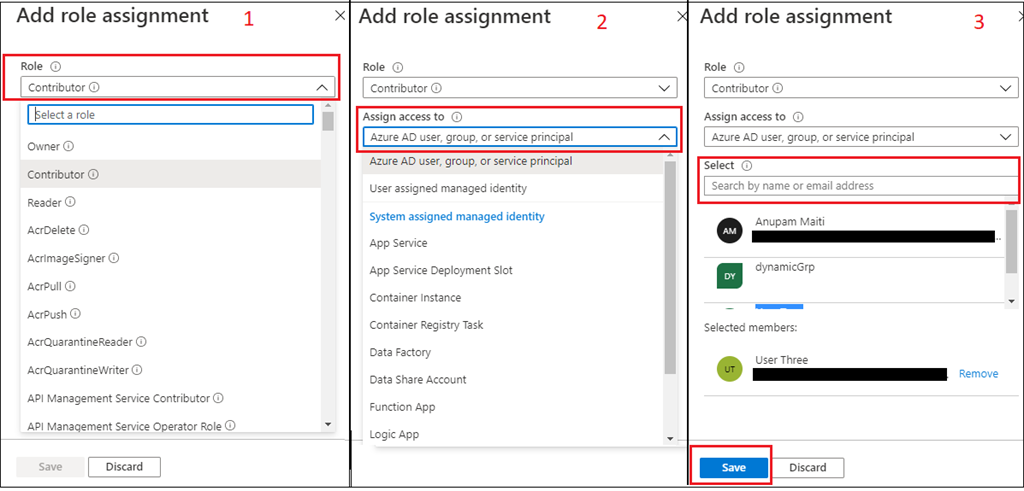
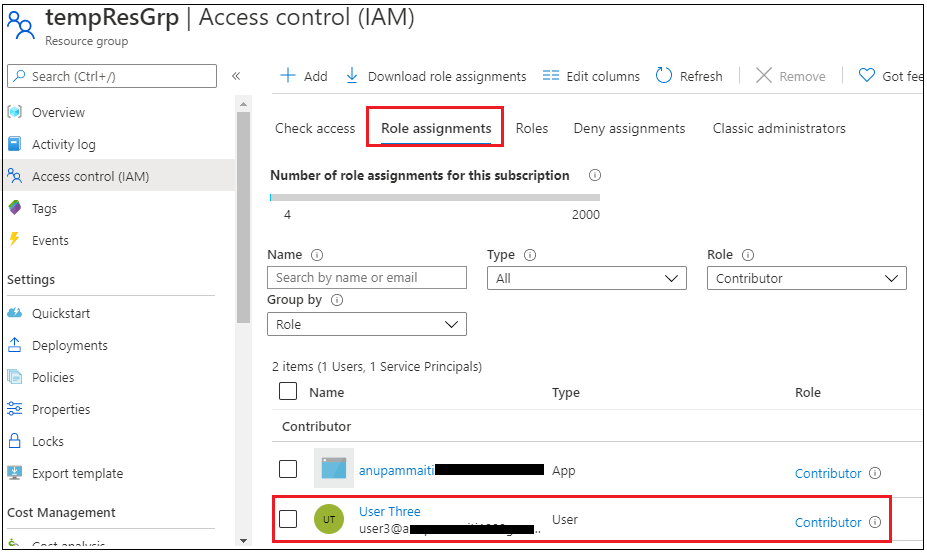
If you happen to now go to the Position assignments tab, you’ll now see the function assigned to the person as a contributor.
Abstract
Azure AD roles are used to handle entry to Azure AD sources, whereas Azure roles are used to handle entry to Azure sources.
The scope of Azure AD roles is on the tenant degree, whereas the scope of Azure roles could be specified at a number of ranges together with administration group, subscription, useful resource group, useful resource.
I hope you discovered this data helpful!