Create An Azure Key Vault With Vault Entry Coverage And Add Secrets and techniques Utilizing ARM Template
On this article, I’ll clarify how we will create an Azure Key vault; add secrets and techniques to an Azure Key Vault, and the way we will add an internet app service principal into the vault entry coverage utilizing easy ARM templates.
Earlier than starting to create an ARM template, the idea right here is that you must have a fundamental understanding of the construction of ARM templates and you have already got a useful resource group.
The Context
For demonstration functions, we are going to create an internet app with a system-assigned identification and we are going to add internet app service principal id to the important thing vault entry coverage. Equally, we are going to create a storage account to display how we will simply add storage account connection string into key vault secret.
We’ll create the under sources on this article for higher understanding functions.
| Useful resource Identify | Sort reference |
| Key Vault | Microsoft.KeyVault/vaults |
| Key Vault – Secret | Microsoft.KeyVault/vaults/secrets and techniques |
| Storage Account | Microsoft.Storage/storageAccounts |
| Net App | Microsoft.Net/websites |
| App Service Plan | Microsoft.Net/serverfarms |
The under picture represents the sources dependency of our ARM templates which we are going to construct in subsequent steps.
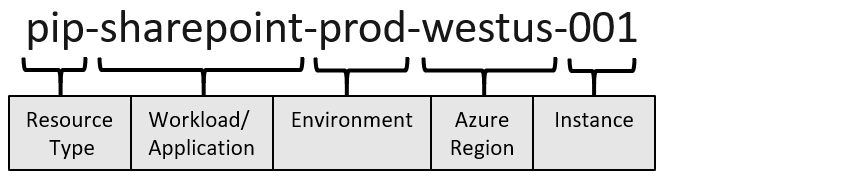
And we are going to comply with the below-maiming conference whereas creating sources utilizing ARM. Picture has been referred from Microsoft documentation.
Let’s construct our template step-by-step for every useful resource.
Parameters & Variables
We’re taking surroundings identify as Enter and within the variable, we are going to concatenate surroundings identify with sources we’re creating.
"parameters": {
"envName": {
"defaultValue": "uat",
"kind": "String"
}
}, "variables": {
"tenantId": "[subscription().tenantId]",
"appServicePlanName": "[concat('plan-myapp-',parameters('envName'),'-',resourceGroup().location)]",
"webAppName": "[concat('app-mywebapp-',parameters('envName'),'-',resourceGroup().location)]",
"storageAccountName": "[concat('stmystorage',parameters('envName'),resourceGroup().location)]",
"keyVaultName": "[concat('kv-myapps-',parameters('envName'),'-',resourceGroup().location)]"
},
Creating Key Vault with Vault Entry Coverage
To create a Key Vault with an entry coverage, we add the next useful resource to the ARM template.
First, we are going to create an internet app with an app service plan.
{
"kind": "Microsoft.Net/serverfarms",
"apiVersion": "2018-02-01",
"identify": "[variables('appServicePlanName')]",
"location": "[resourceGroup().location]",
"sku": {
"identify": "S1",
"tier": "Customary",
"measurement": "S1",
"household": "S",
"capability": 1
},
"sort": "app"
}, {
"kind": "Microsoft.Net/websites",
"apiVersion": "2018-11-01",
"identify": "[variables('webAppName')]",
"location": "[resourceGroup().location]",
"dependsOn": ["[resourceId('Microsoft.Web/serverfarms', variables('appServicePlanName'))]"],
"sort": "app",
"identification": {
"kind": "SystemAssigned"
},
"properties": {
"identify": "[variables('webAppName')]",
"httpsOnly": true,
"serverFarmId": "[resourceId('Microsoft.Web/serverfarms', variables('appServicePlanName'))]"
}
},
Let’s create a key vault with an entry coverage. Right here, we included an entry coverage because the service principal id of an internet app that we’re creating. This can make sure that our internet app reads the connection string straight from Key Vault as we’re implementing Managed Service Identification.
{
"kind": "Microsoft.KeyVault/vaults",
"apiVersion": "2021-04-01-preview",
"identify": "[variables('keyVaultName')]",
"location": "[resourceGroup().location]",
"properties": {
"sku": {
"household": "A",
"identify": "Customary"
},
"tenantId": "[variables('tenantId')]",
"accessPolicies": [{
"tenantId": "[variables('tenantId')]",
"objectId": "[reference(concat('Microsoft.Web/sites/',variables('webAppName')), '2018-11-01','Full').identity.principalId]",
"permissions": {
"keys": [],
"secrets and techniques": ["Get"],
"certificates": []
}
}],
"enabledForDeployment": false,
"enabledForDiskEncryption": false,
"enabledForTemplateDeployment": false,
"enableSoftDelete": true,
"enableRbacAuthorization": false,
"vaultUri": "[concat('https://' ,variables('keyVaultName'),'.vault.azure.net/')]",
"provisioningState": "Succeeded"
}
},
Including Storage Account Connection string as a Secret
First, we are going to add a Storage Account useful resource to the ARM template.
{
"kind": "Microsoft.Storage/storageAccounts",
"apiVersion": "2021-04-01",
"identify": "[variables('storageAccountName')]",
"location": "[resourceGroup().location]",
"sku": {
"identify": "Standard_LRS",
"tier": "Customary"
},
"sort": "Storage",
"properties": {
"supportsHttpsTrafficOnly": true
}
},
Now we are going to add a Secret referred to as “StorageAccountConnectionString” that’s relying on the Storage Account and the Key Vault outlined earlier. The worth of this secret is about with a connection string containing the entry key of the Storage Account that we created earlier.
{
"kind": "Microsoft.KeyVault/vaults/secrets and techniques",
"apiVersion": "2021-04-01-preview",
"identify": "[concat(variables('keyVaultName'), '/StorageAccountConnectionString')]",
"location": "[resourceGroup().location]",
"dependsOn": ["[resourceId('Microsoft.KeyVault/vaults', variables('keyVaultName'))]", "[resourceId('Microsoft.Storage/storageAccounts', variables('storageAccountName'))]"],
"properties": {
"worth": "[concat('DefaultEndpointsProtocol=https;AccountName=', variables('storageAccountName'), ';AccountKey=', listKeys(resourceId('Microsoft.Storage/storageAccounts', variables('storageAccountName')),'2017-06-01').keys[0].worth)]"
}
}
Deploying ARM Template utilizing Azure CLI
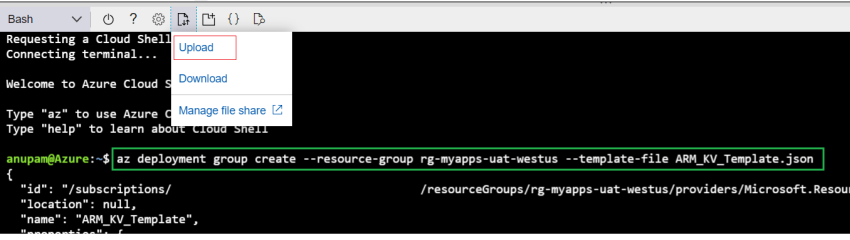
Utilizing Azure CLI, we are going to deploy this template. Right here, my templates identify is “ARM_KV_Template.json” and I’ve a useful resource group created already. First, I uploaded the JSON file utilizing the add possibility after which executed the under script in Bash.
az deployment group create --resource-group rg-myapps-uat-westus --template-file ARM_KV_Template.json
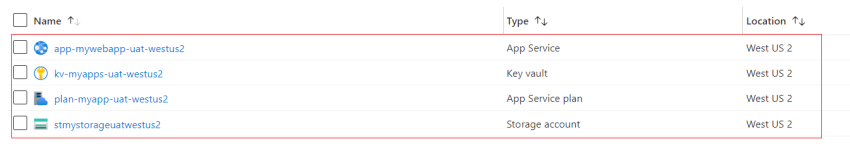
Now should you go to the sources group, you will notice all of the sources are created efficiently.
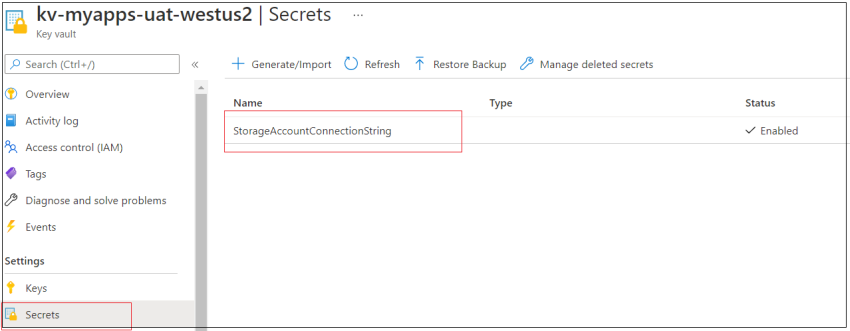
Let’s examine key vault secrets and techniques and entry insurance policies one after the other.
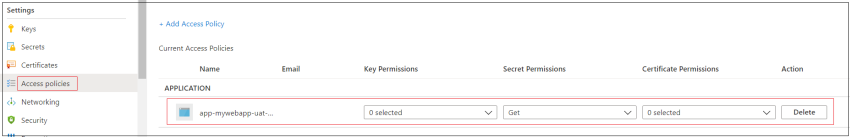
Wonderful! We’re accomplished along with your implementation and we deployed Azure Key vault with an entry coverage and secret utilizing ARM templates.
Hope you discovered this text helpful.
Pleased Studying!