Azure RBAC Position Based mostly Entry Management Demonstration With Azure App Service
Azure supplies a lot versatile role-based entry management for Azure sources by which you’ll be able to effectively handle customers entry to azure sources, can enable the extent of permission, and might establish their entry to varied sources. This entry management known as as Azure role-based entry management i.e., Azure RBAC.
On this article, I’ll present how you can handle role-based entry management type Azure Portal. I’ll show step-by-step Azure RBAC with Azure app service, nonetheless, the method for another sources, teams, and subscriptions is identical.
The primary Step is to login in Azure portal. If you happen to would not have any subscriptions, then you possibly can create a path one.
After login to the azure portal, we are going to see display one thing like as proven under with our latest sources.
We will select anyone the useful resource the place we are able to handle the entry/permissions. In my case, I’m choosing one among my app service, nonetheless the method is identical for each sources/service, useful resource teams, or subscriptions.
After that, we are going to choose Entry Management as proven,
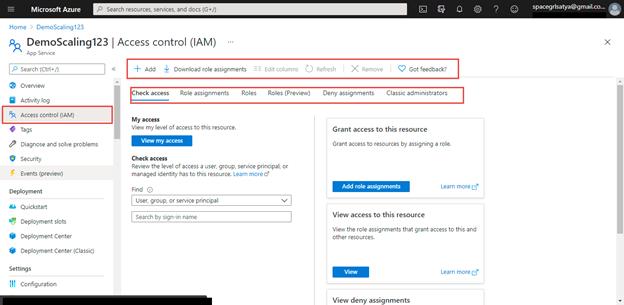
Let me clarify some the choices on this web page.
Add
On clicking this, we are going to get choice for position project or co-administrator.
Obtain position assignments
We will obtain the exiting position assignments in a csv or json file.
Verify entry
We will examine the entry particulars of any consumer, group, or service principal. Moreover, we are able to view present consumer entry.
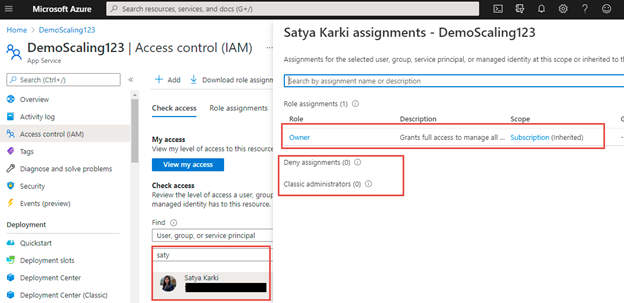
Position Assignments
This selection will give the record of customers, teams and repair principals with their position and scopes who’re gaining access to this app service as given.
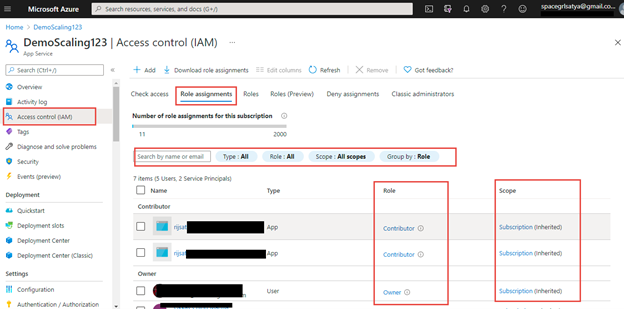
I’ve highlighted the required areas on this position assignments record view. We will all of the customers with their position and scope. Moreover, we are able to use filters of various varieties.
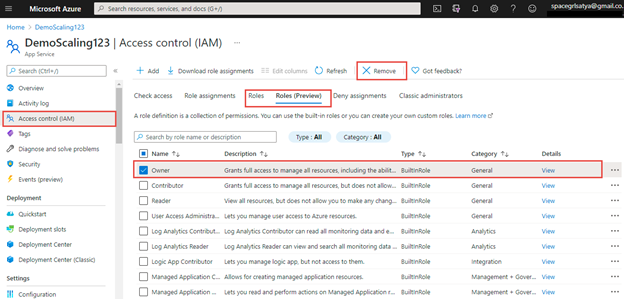
Roles and Roles (Preview)
Roles choice offers record of all of the roles obtainable, each built-in and customized created. Roles (preview) offers position with descriptions. We will add customized roles and might take away any roles from this display.
Deny Assignments
This selection will present you record of deny entry. Deny assignments block customers from performing particular actions even when a task project grants them entry. At the moment, the one means you possibly can add your personal deny assignments is by utilizing Azure Blueprints.
Basic Directors
Listing of directors. Additionally, we could have choice to take away the administrator based mostly on permissions.
Grant Entry or Add Position Assignments
On this part, I’ll present how you can present entry to useful resource by assigning position to consumer(s) or group(s). We will do position assignments from the 2 choices as proven:
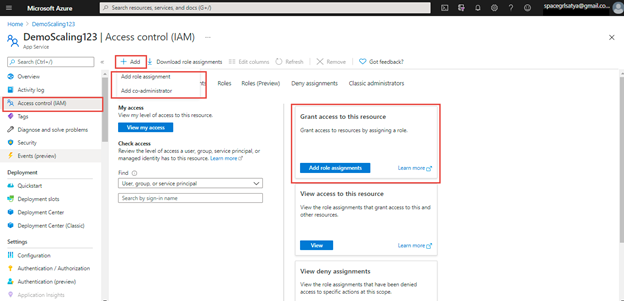
As proven in above picture with highlighted pink, we are able to do position assignments to customers with two choices.
First, Click on on Add position project then we are going to get choices as depicted.
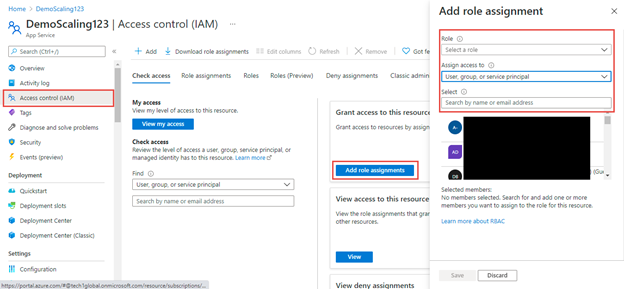
We are going to get three choices to decide on: Position, Assign entry to (sort of customers/safety principal) and Choose (customers).
Position
we use this selection to pick the position which we’re going to assign. Listed below are the record roles obtainable to azure app service:
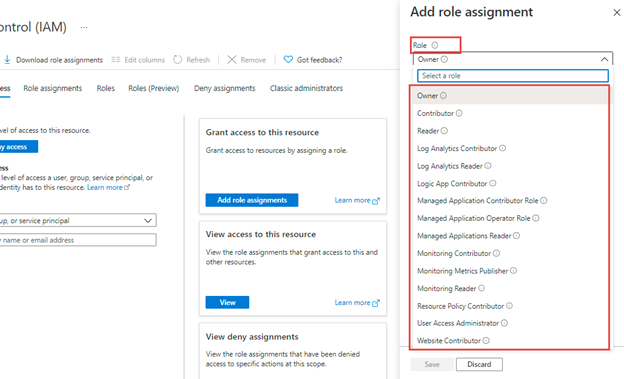
There are a number of roles obtainable for this app service like proprietor, contributor, reader, log analytics associated, managed software associated, monitoring associated, consumer entry administrator, web site contributor and so on.
Notice: Position record could be completely different based mostly on the sources like azure app service, azure SQL service, azure VM, useful resource group, subscriptions and so on. could have completely different roles varieties.
Nonetheless, there are some widespread roles like proprietor, contributor, reader and so on. to each azure sources.
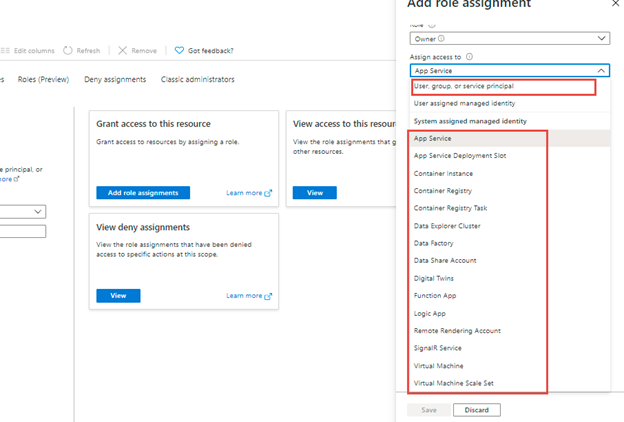
Assign entry to
This selection means to assign entry to customers, group, or safety principal. Moreover, we can provide entry to system assigned managed identification like one other app service, container occasion, azure sources like information manufacturing unit, operate app, logic app, signalR Service, VMs likewise.
We can provide entry to system managed identification of different subscriptions in addition to proven,
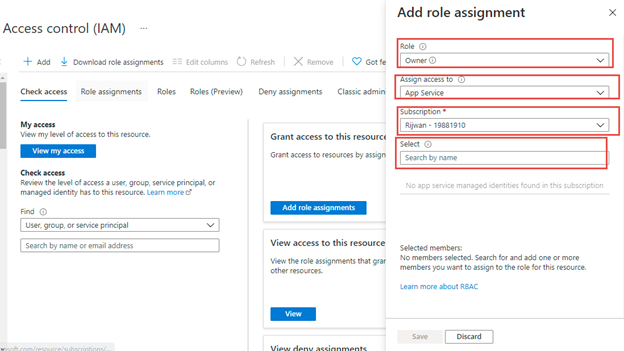
After choosing position after which entry to love azure app, or another system managed identification then we are going to get choice to pick subscription and useful resource type that subscription as portrayed:
Equally, if we choose consumer, group, or service principal then we are going to get choice choose customers or teams as proven under,
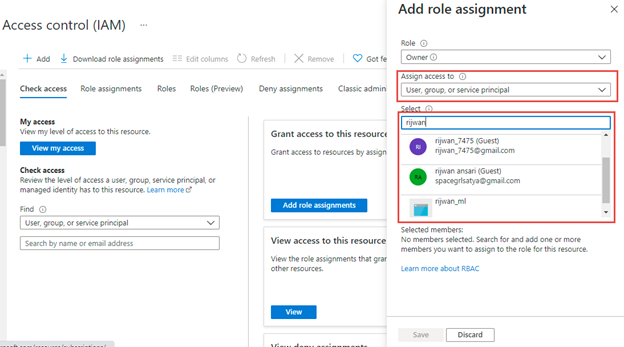
Notice
we are able to search and add single or a number of customers from our group or visitor customers.
Lastly, we are able to grant entry to customers by choosing a task, assign entry to, customers and put it aside as depicted.
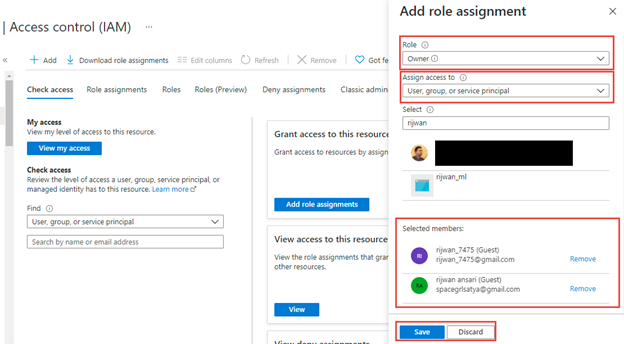
That is how, we are able to assign or grant entry to azure sources that known as as Azure RBAC role-based entry management.
Conclusion
On this article, I’ve demonstrated how you can grant entry to azure sources in particulars which can also be referred to as as Azure RBAC role-based entry management. I’ve exemplified step-by-step utilizing Azure App service with full Azure RBAC and obtainable further choices. Nonetheless, the processes are identical for an additional azure sources, useful resource teams, and subscriptions. Then once more, position record/choices may be completely different based mostly on sort of sources.