Azure Key Vault – From {Hardware} To The Cloud!
Introduction – from {Hardware} to the Cloud!
A {hardware} safety module (HSM) is a bodily computing system which safeguards and manages digital keys. They’re used when safety is necessary and embody options reminiscent of auditing, tamper-proofing and encryption. Nonetheless, as with all {hardware} gadgets there’s expense and work concerned in procuring, putting in, upgrading and sustaining an HSM. That is the place Azure Key Vault is available in. It offers the safety of an HSM, however with out the work of setting it up or sustaining it
What’s Azure Key Vault used for?
No matter is saved in Azure Key Vault is safeguarded utilizing industry-standard algorithms, HSMs and key lengths. The HSMs are Degree 2 validated for Federal Info Processing Normal (FIPS). Microsoft offers the interface with which you’ll be able to entry the HSM system securely. For extra assurance in regards to the integrity of the important thing, you possibly can generate it contained in the HSM. Microsoft can’t entry or extract your keys. Purposes additionally haven’t any direct entry to the keys. As a substitute you’ll have to make use of Azure CLI, Portal or PowerShell as an interface.
Azure Key Vault can be utilized for key administration because it makes it straightforward to create and management the encryption keys used to encrypt your keys. It can be used for certificates administration to allow you to simply provision, handle and deploy Safe Sockets Layer/Transport Layer Safety (SSL/TLS).
Azure Key Vault helps three varieties of information, together with:
- Secrets and techniques. These are values which can be 25KB or much less. They’re written to and skim from and can be utilized to retailer passwords, entry keys or SQL join strings.
- Keys. These are written to the important thing vault however can’t be exported. They’re used for encryption and hash era. Even when the bottom line is used it may be configured to not depart the HSM and as an alternative the cipher operations required are despatched to the important thing vault service and the consequence returned.
- Information. Delicate items of knowledge can be saved in Azure Key Vault.
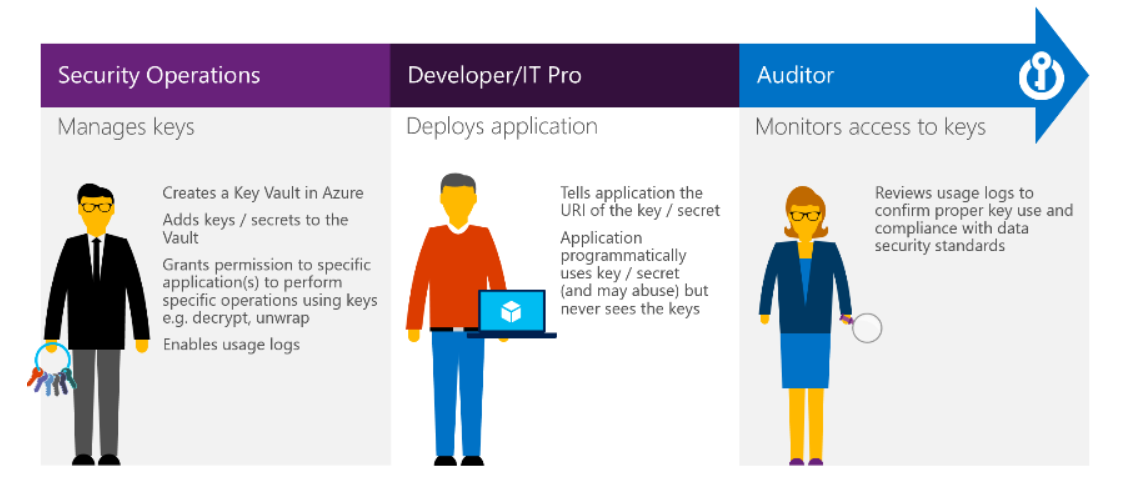
When utility secrets and techniques are centrally saved in Azure Key Vault, it’s simpler to regulate their distribution. There’s now not any want for utility builders to retailer safety data of their utility, so that they now not have to make this data a part of the code.
How does it work?
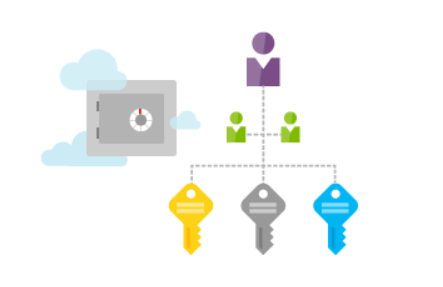
No-one (a consumer or an utility) can get entry to Azure Key Vault until they’ve correct authentication and authorization. The identification of the caller is established by means of authentication. That is executed through the Azure Lively Listing. Authorization determines what operations the caller is allowed to hold out. Authorization will be executed utilizing role-based entry management (RBAC) or Key Vault entry coverage.
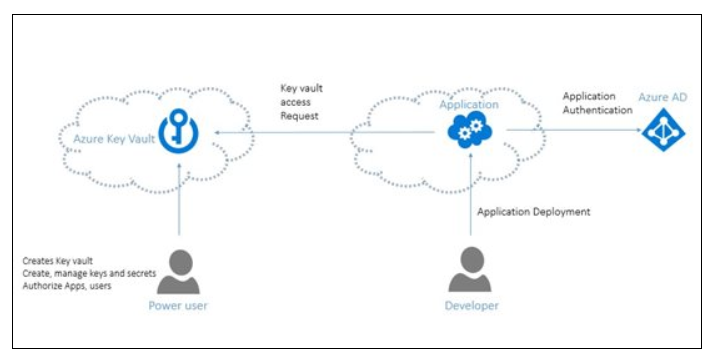
Entry to a key vault requires correct authentication and authorization earlier than a caller (consumer or utility) can get entry. Authentication establishes the identification of the caller, whereas authorization determines the operations that they’re allowed to carry out.
Azure Key Vault additionally lets you segregate utility secrets and techniques. You may prohibit functions entry solely to the vault that you simply enable; for instance, you possibly can create a Key Vault for every particular utility and its workforce of builders.
What sort of operations are supported?
- For keys: Create, Import, Get, Record, Backup, Restore, Delete, Replace, Signal, Confirm, Wrap, Unwrap, Encrypt & Decrypt
- For Secrets and techniques: Create, Replace, Get, Record, Delete
- For Certificates: Create, Replace Coverage, Contacts, Import, Renewal, Replace
How is Azure Key Vault managed?
Key Vault administration is allowed through REST, CLI, PowerShell and Azure Useful resource Supervisor. All keys and secrets and techniques added to Azure Key Vault have their very own URL. Purposes can entry the keys they want by utilizing the URLs, so there’s no want to put in writing code to guard the key data. Key Vault additionally has logging options. This makes it potential to observe when and who accessed the contents of the Key Vault. The entry logs are saved into an Azure storage account.
Simplified administration
Useful information have to be secured, but in addition have to be extremely obtainable. Utilizing Azure Key Vault simplifies lots of the administration wanted to safe secrets and techniques.
- It could possibly scale up rapidly when wanted.
- You may copy the contents of your key vault inside a area and to a different area to enhance availability.
- It may be simply accessed through the portal, Azure CLI and PowerShell.
- Some duties associated to certificates will be automated.
Integration with different Azure providers
Key Vault can be utilized to simplify Azure Information Encryption, the all the time encrypted performance in Azure SQL Database. Key Vault can even combine with storage accounts, log analytics and occasion hubs.