RBAC vs Vault Entry Coverage in Azure Key Vault
Azure Key Vault is a important service for managing secrets and techniques, keys, and certificates utilized by cloud purposes and companies. To make sure safe and managed entry to the assets saved in Azure Key Vault, Azure gives two major strategies of entry management: Function-Primarily based Entry Management (RBAC) and Vault Entry Coverage. This text explores the variations between these two strategies and their use circumstances and gives step-by-step directions on tips on how to configure every.
Overview
- Function-Primarily based Entry Management (RBAC): RBAC is a technique for managing entry to Azure assets based mostly on roles assigned to customers, teams, and purposes. RBAC permits fine-grained management over entry and permissions throughout the Azure ecosystem.
- Vault Entry Coverage: Vault Entry Coverage is a Key Vault-specific entry management technique that means that you can grant permissions to secrets and techniques, keys, and certificates independently. It gives a extra granular stage of management throughout the Key Vault.
Key Variations Between RBAC and Vault Entry Coverage
| Characteristic/Facet | Function-Primarily based Entry Management (RBAC) | Vault Entry Coverage |
| Scope | Broad could be utilized to all Azure assets | Particular to Azure Key Vault |
| Granularity | Function-based, could be fine-grained on the useful resource stage | Object-specific (secrets and techniques, keys, certificates) |
| Administration | Managed by means of Azure portal, CLI, PowerShell | Managed instantly in Key Vault |
| Integration | Built-in with Azure AD roles and permissions | Impartial of Azure AD roles, particular to Key Vault |
| Flexibility | Excessive, can apply to a number of assets and companies | Centered, detailed management throughout the Key Vault |
| Use Case | Broad entry management wants throughout a number of companies | Detailed, particular entry management throughout the Key Vault |
Use Instances
RBAC
- Broad administrative management: Assign broad entry to directors throughout a number of assets.
- Function-based entry: Assign particular roles to customers/teams for entry to numerous Azure assets.
- Integration with Azure AD: Make the most of present Azure AD roles and insurance policies for streamlined entry administration.
Vault Entry Coverage
- Advantageous-grained management: Assign permissions to particular secrets and techniques, keys, or certificates.
- Utility-specific entry: Present entry to explicit purposes or companies with out broader permissions.
- Impartial administration: Handle Key Vault entry independently of Azure AD roles.
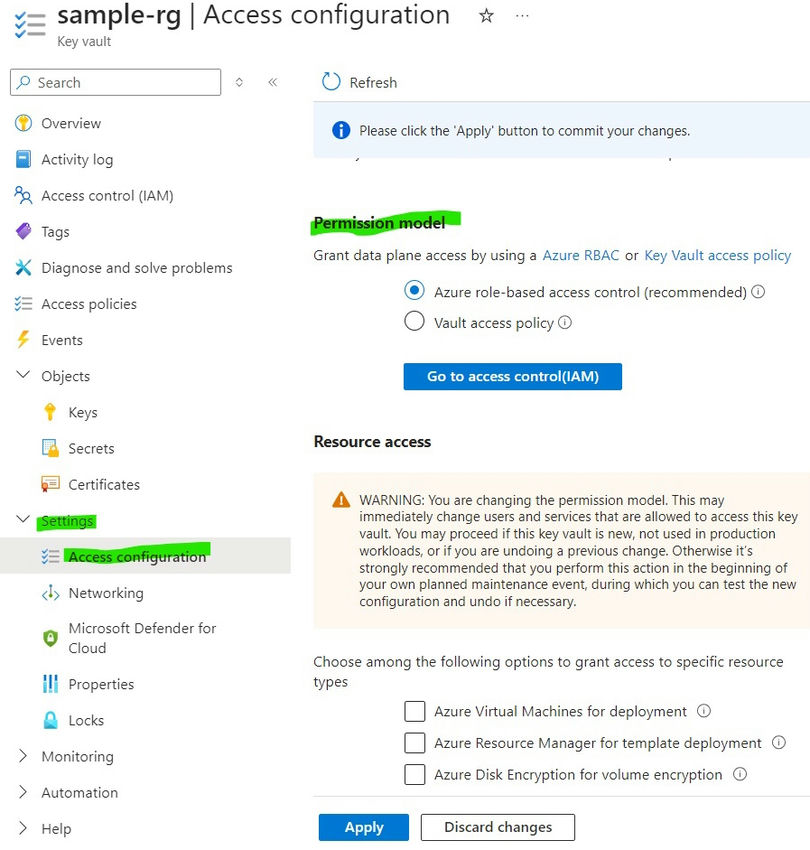
Switching Between RBAC and Vault Entry Coverage
Azure Key Vault means that you can use both RBAC or Vault Entry Insurance policies, however not each concurrently. Right here’s tips on how to change between the 2:
- Open Azure Portal
- Find Key Vault
- Go to All Companies> Key Vault and choose your Key Vault.
- Settings
- Go to Settings > Entry Configuration.
- Change Configuration
- Choose Azure role-based entry management/Entry Coverage to modify.
- Click on Save
Conclusion
Each Function-Primarily based Entry Management (RBAC) and Vault Entry Coverage supply sturdy methods to handle entry to Azure Key Vault, every with its distinctive benefits. RBAC gives broad, role-based entry management throughout Azure assets, making it appropriate for organizations with various useful resource administration wants. Vault Entry Coverage, then again, presents detailed, object-specific entry management throughout the Key Vault, superb for purposes requiring exact permissions.
Understanding these variations and tips on how to configure every technique means that you can implement probably the most applicable entry management technique to your Azure Key Vault deployments.
Know extra about our firm at Skrots. Know extra about our companies at Skrots Companies, Additionally checkout all different blogs at Weblog at Skrots