Overview of Azure Key Vault ?
Introduction
On this article, you’ll find out about Azure Key Vault.
Stipulations
Earlier than you perceive the Azure key vault, I like to recommend it’s best to have a:
- Fundamental data of software program implementation
- Fundamental data of Microsoft Azure
Background
Microsoft Azure has so much many providers associated to storing info within the information sources, operating the enterprise logic, AI, ML, and so forth. BUT, it is vitally essential to have a safe mechanism to retailer essential info. This may be achieved utilizing Azure key vault service.
Azure Key vault
Historically, for encryption of business-critical information safety, connection strings, passwords, secrets and techniques keys, PFX recordsdata, API keys, certificates particulars, secured keys, and so forth. are saved utilizing a few methods These embody storing them in configuration recordsdata like net.config, encrypting this info and utilizing it in enterprise logic by decrypting it.
Microsoft Azure has one service to safe your secret info, Azure key vault. With this, the developer now not wants to make use of this info within the software code stage or within the software configuration stage. It is vitally safe, because the software and even Microsoft has no direct entry to this info. Solely the person can grant permission to entry it or use it. The event staff can use the encryption keys to encrypt the information and retailer it within the Azure key vault. We will even handle Safe Sockets Layer/Transport Layer Safety (SSL/TLS) certificates through the use of this service. Azure key vault info is secured by numerous methods like software program or FIPS 140-2 Degree 2 validates {hardware} safety modules. A certified person can create, import, encrypt, decrypt the encryption keys shortly in a minute.
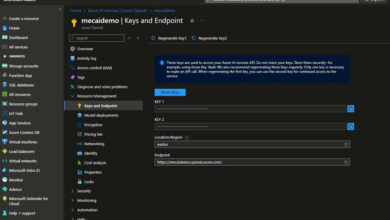
It has a key-value pair. We will create and handle this info through the use of the Azure portal. The data of the Azure key vault will be accessed utilizing the URI. Entry to a key vault requires correct authentication and authorization earlier than a caller (person or software) can get entry. Keys are safeguarded by Azure, utilizing industry-standard algorithms, key lengths, and {hardware} safety modules. If we use the Azure key vault characteristic, then we will handle the secrets and techniques centrally in a single place in essentially the most safe manner.
Authentication with Azure key vault is completed by Azure energetic listing and authorization will be achieved through the use of role-based entry (RBAC) safety mechanism. Azure key vault will be monitored with the log’s info, which must be enabled.
Azure key-vault keys and secrets and techniques are utterly managed and guarded with out writing extra code to guard and safe them. The event staff will focus solely on implementing the software program modern options. Key-vault admin will be buyer will be capable of handle/change their secret keys. The applying doesn’t have direct entry to keys for extra safety.
We will create and handle these providers through the use of Cloud CLI, PowerShell, Azure net portal, Python, JAVA, Node.JS, .NET, Azure Useful resource Administration (ARM) template, REST API, and so forth.
Briefly, Azure key-vault a good way to securely retailer secrets and techniques.
It is strongly recommended to make use of this characteristic to:
- Retailer business-critical secrets and techniques like certificates, connection strings, and passwords and so forth.
- Use Azure key vault per software per atmosphere. This helps to not share the keys between environments.
- Make certain to usually backup the Azure key vault.
- Set an alert and allow it is logging.
- Activate the restoration possibility.
Conclusion
On this article, we’ve got discovered about Azure software safety utilizing Azure key vault service. Within the subsequent article, we’ll study Azure key vault phrases and the way it works internally.
I’ll preserve writing, keep tuned!