Azure Firewall Supervisor is now typically obtainable
Azure Firewall Supervisor is now typically obtainable and consists of Azure Firewall Coverage, Azure Firewall in a Digital WAN Hub (Safe Digital Hub), and Hub Digital Community. As well as, we’re introducing a number of new capabilities to Firewall Supervisor and Firewall Coverage to align with the standalone Azure Firewall configuration capabilities.
Key options on this launch embody:
- Menace intelligence-based filtering enable listing in Firewall Coverage is now typically obtainable.
- A number of public IP addresses help for Azure Firewall in Safe Digital Hub is now typically obtainable.
- Compelled tunneling help for Hub Digital Community is now typically obtainable.
- Configuring safe digital hubs with Azure Firewall for east-west visitors (personal) and a third-party safety as a service (SECaaS) associate of your alternative for north-south visitors (web sure).
- Integration of third-party SECaaS companions are actually typically obtainable in all Azure public cloud areas.
- Zscaler integration will probably be typically obtainable on July 3, 2020. Verify Level is a supported SECaaS associate and will probably be in preview on July 3, 2020. iboss integration will probably be typically obtainable on July 31, 2020.
- Help for area identify system (DNS) proxy, customized DNS, and fully-qualified area identify (FQDN) filtering in community guidelines utilizing Firewall Coverage are actually in preview.
Firewall Coverage is now typically obtainable
Firewall Coverage is an Azure useful resource that accommodates community tackle translation (NAT), community, and utility rule collections, in addition to menace intelligence and DNS settings. It’s a world useful resource that can be utilized throughout a number of Azure Firewall situations in Secured Digital Hubs and Hub Digital Networks. Firewall insurance policies work throughout areas and subscriptions.
You don’t want Firewall Supervisor to create a firewall coverage. There are lots of methods to create and handle a firewall coverage, together with utilizing REST API, PowerShell, or command-line interface (CLI).
After you create a firewall coverage, you’ll be able to affiliate the coverage to a number of firewalls utilizing Firewall Supervisor or utilizing REST API, PowerShell, or CLI. Seek advice from the policy-overview doc for a extra detailed comparability of guidelines and coverage.
Migrating standalone firewall guidelines to Firewall Coverage
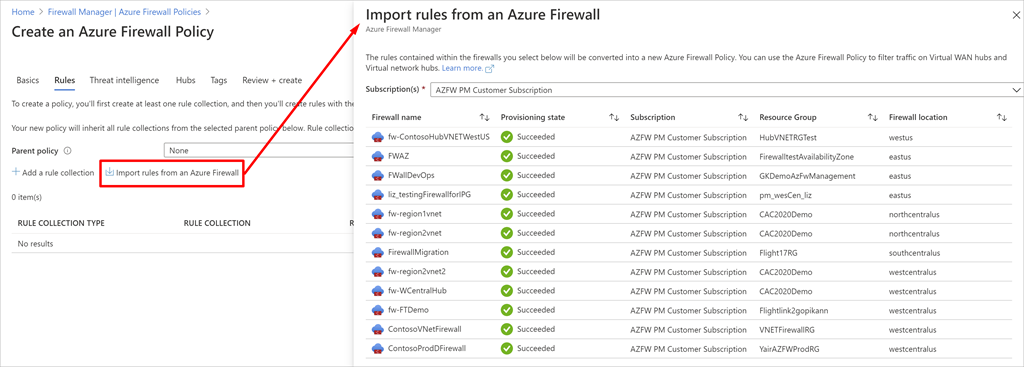
It’s also possible to create a firewall coverage by migrating guidelines from an present Azure Firewall. You should utilize a script emigrate firewall guidelines to Firewall Coverage, or you should utilize Firewall Supervisor within the Azure portal.
Importing guidelines from an present Azure Firewall.
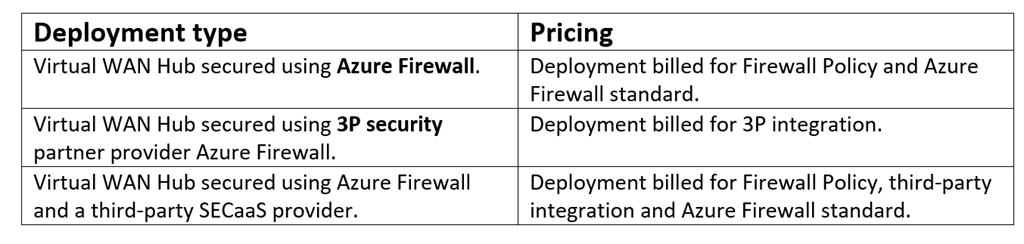
Firewall Coverage pricing
For those who simply create a Firewall Coverage useful resource, it doesn’t incur any expenses. Moreover, a firewall coverage shouldn’t be billed whether it is related to only a single Azure firewall. There are not any restrictions on the variety of insurance policies you’ll be able to create.
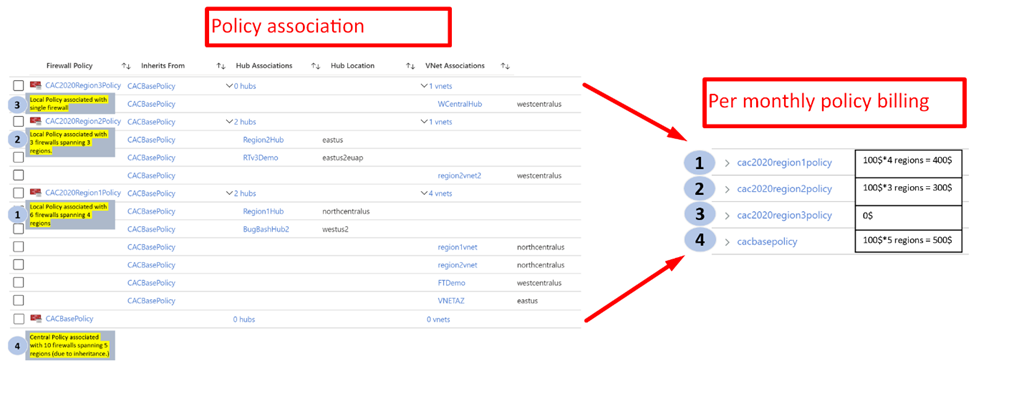
Firewall Coverage pricing is fastened per Firewall Coverage per area. Inside a area, the value for Firewall Coverage managing 5 firewalls or 50 firewalls is identical. The next instance makes use of 4 firewall insurance policies to handle 10 distinct Azure firewalls:
- Coverage 1: cac2020region1policy—Related to six firewalls throughout 4 areas. Billing is completed per area, not per firewall.
- Coverage 2: cac2020region2policy—Related to three firewalls throughout three areas and is billed for 3 areas whatever the variety of firewalls per area.
- Coverage 3: cac2020region3policy—Not billed as a result of the coverage shouldn’t be related to a couple of firewall.
- Coverage 4: cacbasepolicy—A central coverage that’s inherited by all three insurance policies. This coverage is billed for 5 areas. As soon as once more, the pricing is decrease in comparison with per-firewall billing strategy.
Firewall Coverage billing instance.
Configure a menace intelligence enable listing, DNS proxy, and customized DNS
With this replace, Firewall Coverage helps extra configurations together with customized DNS and DNS proxy settings (preview) and a menace intelligence enable listing. SNAT Non-public IP tackle vary configuration shouldn’t be but supported however is in our roadmap.
Whereas Firewall Coverage can sometimes be shared throughout a number of firewalls, NAT guidelines are firewall particular and can’t be shared. You’ll be able to nonetheless create a dad or mum coverage with out NAT guidelines to be shared throughout a number of firewalls and a neighborhood derived coverage on particular firewalls so as to add the required NAT guidelines. Study extra about Firewall Coverage.
Firewall Coverage now helps IP Teams
IP Teams is a brand new top-level Azure useful resource in that permits you to group and handle IP addresses in Azure Firewall guidelines. Help for IP Teams is roofed in additional element in our current Azure Firewall weblog.
Configure secured digital hubs with Azure Firewall and a third-party SECaaS associate
Now you can configure digital hubs with Azure Firewall for personal visitors (digital community to digital community/department to digital community) filtering and a safety associate of your alternative for web (digital community to web/department to web) visitors filtering.
A safety associate supplier in Firewall Supervisor permits you to use your acquainted, best-in-breed, third-party SECaaS providing to guard web entry to your customers. With a fast configuration, you’ll be able to safe a hub with a supported safety associate, and route and filter web visitors out of your digital networks (VNets) or department places inside a area. That is finished utilizing automated route administration, with out organising and managing Consumer Outlined Routes (UDRs).
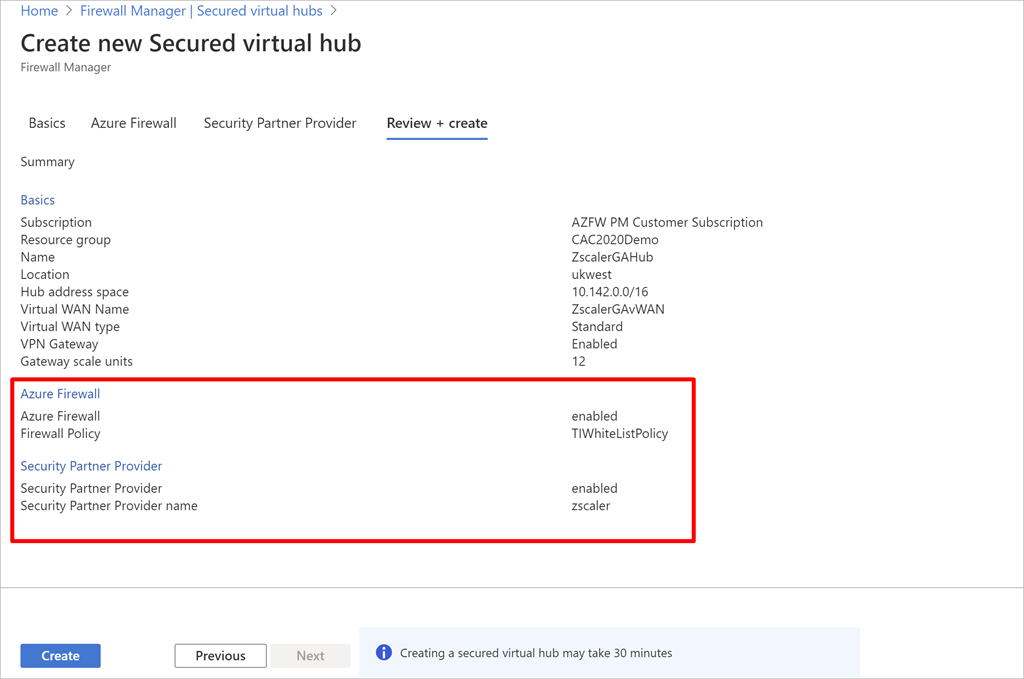
You’ll be able to create a safe digital hub utilizing Firewall Supervisor’s Create new secured digital hub workflow. The next screenshot reveals a brand new safe digital hub configured with two safety suppliers.
Creating a brand new safe digital hub configured two safety suppliers.
Securing connectivity
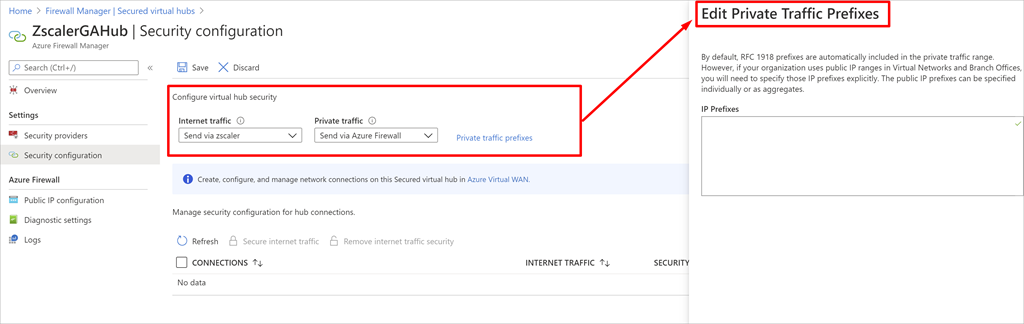
After you create a safe hub, it’s essential to replace the hub safety configuration and explicitly configure the way you need web and personal visitors within the hub to be routed. For personal visitors, you don’t have to specify prefixes if it’s within the RFC1918 vary. In case your group makes use of public IP addresses in digital networks and branches, it’s essential to add these IP prefixes explicitly.
To simplify this expertise, now you can specify combination prefixes as a substitute of specifying particular person subnets. Moreover, for web safety by way of a third-party safety supplier, it’s essential to full your configuration utilizing the associate portal. Please see the safety associate supplier web page for extra particulars.
Deciding on a third-party SECaaS for web visitors filtering.
Secured digital hub pricing
A secured digital hub is an Azure Digital WAN Hub with related safety and routing insurance policies configured by Firewall Supervisor. Pricing for secured digital hubs will depend on the safety suppliers configured.
See the Firewall Supervisor pricing web page for added particulars.
Subsequent steps
For extra info on these bulletins, see the next sources: