Migrate to Azure Defender from Qualys Vulnerability Evaluation
Introduction
&nbs
Microsoft Defender for Cloud merges all vulnerability evaluation options to make the most of the Microsoft Defender Vulnerability Administration vulnerability scanner. As a part of this transition, the Defender for Cloud Containers Vulnerability Evaluation powered by Qualys has been retired. https://study.microsoft.com/en-us/azure/defender-for-cloud/release-notes#defender-for-cloud-containers-vulnerability-assessment-powered-by-qualys-retirement
If you happen to haven’t made the change but, observe the steps beneath to seamlessly transition to vulnerability assessments for Azure utilizing Microsoft Defender Vulnerability Administration.
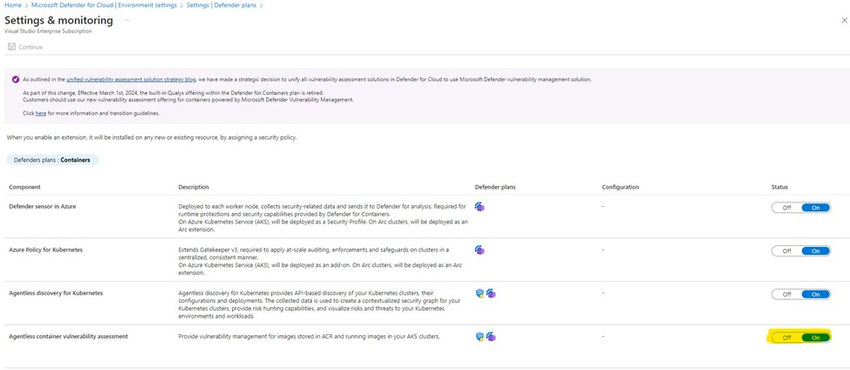
Step 1. Confirm scanning enablement
Container vulnerability evaluation scanning powered by Microsoft Defender Vulnerability Administration is enabled by default for the next companies.
- Defender for Containers
- Defender for Container Registries (deprecated)
- Defender Cloud Safety Posture Administration
In case your group disabled scanning, you should re-enable the Agentless container vulnerability evaluation toggle in one of many plans. This transformation will routinely replicate throughout the talked about plans.
Step 2. Replace REST API and Azure useful resource graph queries (optionally available)
If you happen to have been accessing container vulnerability evaluation outcomes by way of Qualys (utilizing Azure Useful resource Graph (ARG) REST API or Sub evaluation REST API), you’ll have to replace your present queries saved in Azure Useful resource Graph. Confirm they match the brand new schema and REST API supplied by the container vulnerability evaluation printed by Microsoft Defender Vulnerability Administration.
Listed below are a couple of examples that will help you transition your queries:
Instance. Present unhealthy container pictures
Qualys question (Azure Useful resource Graph)
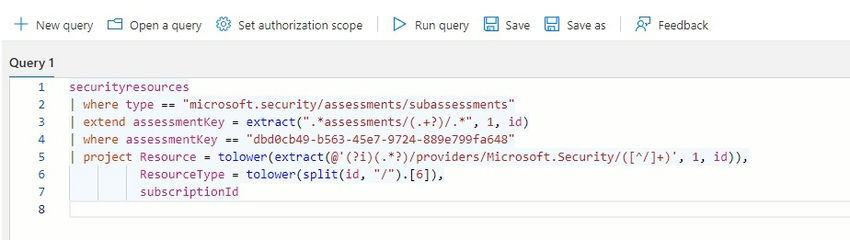
| securityresources |
| | the place kind == “microsoft.safety/assessments/subassessments” |
| | lengthen assessmentKey = extract(“.*assessments/(.+?)/.*”, 1, id) |
| | the place assessmentKey == “YOUR_NEW_ASSESSMENT_KEY” |
| | venture Useful resource = tolower(extract(@'(?i)(.*?)/suppliers/Microsoft.Safety/([^/]+)’, 1, id)), |
| ResourceType = tolower(cut up(id, “/”).[6]), |
| subscriptionId |
Replace to Microsoft Defender vulnerability administration question
| securityresources |
| | the place kind == “microsoft.safety/assessments/subassessments” |
| | lengthen assessmentKey = extract(“.*assessments/(.+?)/.*”, 1, id) |
| | the place assessmentKey == “YOUR_NEW_ASSESSMENT_KEY” |
| | venture Useful resource = tolower(extract(@'(?i)(.*?)/suppliers/Microsoft.Safety/([^/]+)’, 1, id)), |
| ResourceType = tolower(cut up(id, “/”).[6]), |
| subscriptionId |
Keep in mind to interchange “YOUR_NEW_ASSESSMENT_KEY” with the appropriate evaluation key.
For extra particulars, go to the official article: Transition to Microsoft Defender Vulnerability Administration.
Know extra about our firm at Skrots. Know extra about our companies at Skrots Companies, Additionally checkout all different blogs at Weblog at Skrots