Apply Azure Digital Machines to the Zero Belief Ideas
Zero Belief
A brand new safety structure referred to as Zero Belief verifies each request as if it got here from an unmanaged community and presumes a breach. This submit will educate you the basics of Zero Belief and give you instruments to place it into observe.
You have to arrange logical isolation with devoted useful resource teams, use role-based entry management (RBAC), safe digital machine boot elements, allow customer-managed keys and double encryption, handle put in apps, configure safe entry and upkeep of digital machines, and allow superior risk detection and safety to use Zero Belief ideas to Azure digital machines.
Three security-related Zero-Belief ideas are as follows.
- Confirm explicitly: Primarily based on all the knowledge at disposal, such because the consumer’s identification, location, machine, classification of well being knowledge, and abnormalities, authenticate and grant entry.
- Use least privilege entry: Scale back consumer entry to risk-based adaptive controls, knowledge safety, and just-in-time companies that safeguard info and effectivity. Moreover, it offers the consumer with as restricted entry to assets as possible to allow them to full their process as shortly as doable.
- Assume breach: divide entry primarily based on community consumer gadgets and software consciousness to cut back the extent of hurt and cease lateral motion. Moreover, verify that your complete session is encrypted.
Step 1. Arrange logical isolation for digital machines.
Step 2. Deploy role-based entry management (RBAC).
You’ll be able to leverage machine standing, knowledge classification, anomalies, location, and identification with the Managed Id and Conditional Entry Coverage to impose multifactor authentication and selectively grant entry primarily based on verified belief.
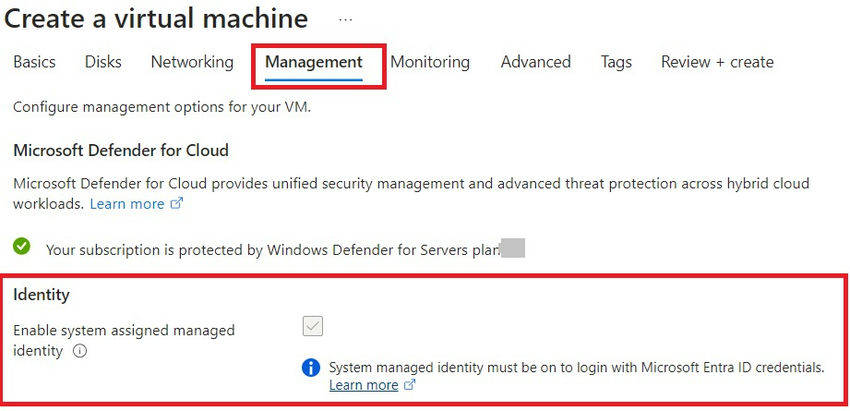
Go to the digital machine’s administration blade and activate System Assigned Managed Id, as demonstrated right here, to broaden your management past the system and allow secure entry on your Microsoft Entra ID tenant utilizing Microsoft Clever Safety Graph.
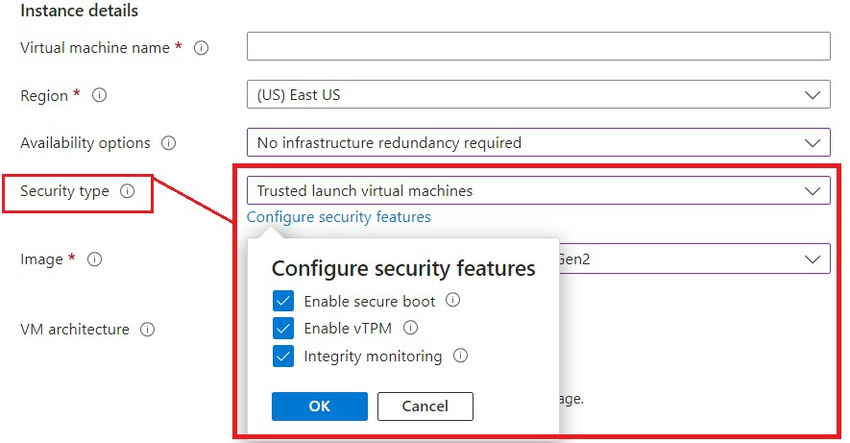
Step 3. Safe elements utilized in digital machine boot-up.
Ensure that the boot elements’ safety is configured whenever you assemble the digital machine. You need to use vTPM and Safe Boot along with selecting a safety sort with enhanced digital machine deployment.
Be sure the duties are dependable and verifiable. By monitoring your digital machine’s full boot chain, which incorporates the UEFI, OS, system, and drivers, the vTPM makes attestation doable.
Step 4. Double encryption and customer-managed keys are enabled.
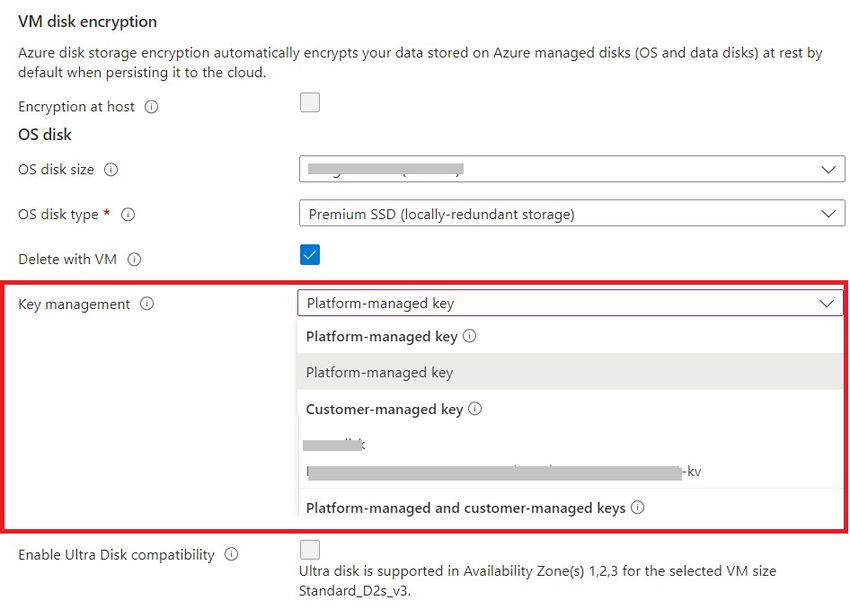
For the digital machine settings, you select the encryption sort on the disk blade. As seen beneath, select Double encryption with platform-managed and customer-managed keys underneath Encryption sort.
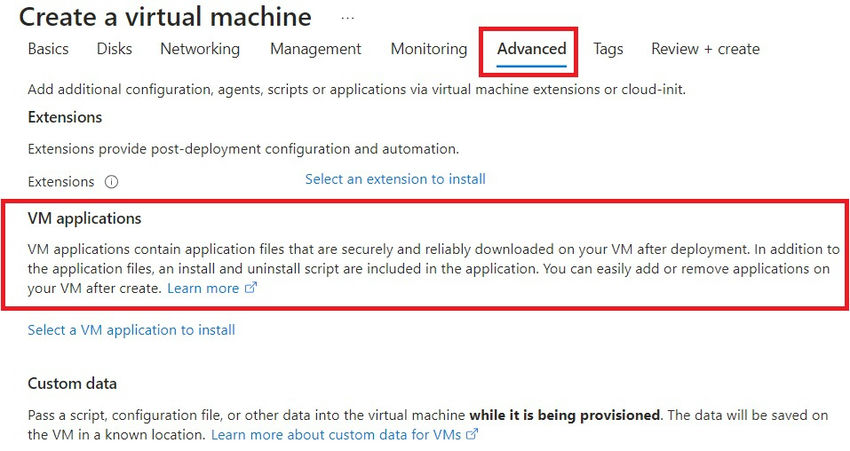
Step 5. Handle the digital machines’ put in applications.
The operate referred to as Digital Machine Functions lets you handle the put in functions on digital machines. You’ll be able to select which functions to put in in your digital laptop with this function.
This performance streamlines digital machine software administration by using the Azure Compute Gallery. You might be sure that customers can entry solely trusted functions by combining RBAC with it.
Step 6. Arrange safe entry.
To arrange secure entry
- Arrange secure communication between elements within the Azure setting which have direct entry to digital machines.
- Configure conditional entry along with multifactor authentication.
- Make the most of workstations with privileged entry (PAWs)
Step 7. Configure digital machine safety upkeep.
Secure digital machine upkeep consists of the next.
- Anti-malware software program
- digital machine replace automation
Step 8. Activate highly effective protection and risk identification
Microsoft Defender for Cloud gives risk prevention for Azure infrastructure. While you configure Microsoft Defender for Servers, digital machines are additionally lined by this safety.
Abstract
This text describes tips on how to apply Azure digital machines to the Zero Belief ideas. Server-side encryption with customer-managed keys for managed disks shall be lined within the upcoming submit.
Know extra about our firm at Skrots. Know extra about our companies at Skrots Providers, Additionally checkout all different blogs at Weblog at Skrots