App Registration with Microsoft Entra ID Configure SharePoint Permissions
Introduction
On this article, you’ll learn to register an app with Microsoft Entra ID and configure SharePoint permissions utilizing PowerShell. The script will carry out the next actions.
- Register a brand new utility in Microsoft Entra ID.
- Configure the required SharePoint permissions.
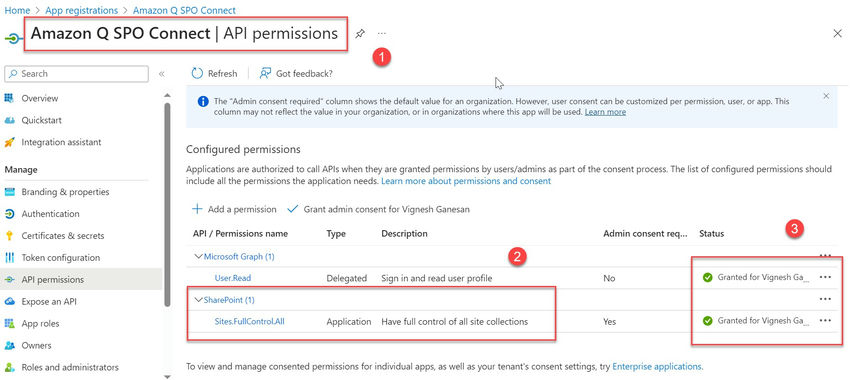
- Present admin consent for the permissions.
Conditions
- Set up the Microsoft Graph PowerShell SDK.
- Microsoft Entra ID administrator permissions to create and configure app registration.
- Create a self-signed certificates by executing Create-SelfSignedCertificate.ps1.
Steps Concerned
Carry out the next steps to register an app with Microsoft Entra ID and configure SharePoint permissions utilizing PowerShell.
Open Home windows PowerShell ISE. Copy and paste the under script.
param(
[Parameter(Mandatory=$true,
HelpMessage="The friendly name of the app registration")]
[String]
$AppName,
[Parameter(Mandatory=$true,
HelpMessage="The file path to your public key file")]
[String]
$CertPath,
[Parameter(Mandatory=$false,
HelpMessage="Your Azure Active Directory tenant ID")]
[String]
$TenantId,
[Parameter(Mandatory=$false)]
[Switch]
$StayConnected = $false
)
# Show the choices for permission
$validOptions = @('F', 'S')
Write-Host "Choose the permissions: [F]-sites.FullControl.All [S]-sites.Chosen"
# Loop to immediate the person till a legitimate possibility is chosen
do {
foreach ($possibility in $validOptions) {
Write-Host "[$option]"
}
$selectedPermission = Learn-Host "Enter your selection (F, or S)"
} whereas ($selectedPermission -notin $validOptions)
# Map person enter to corresponding permissions
$permissionMapping = @{
'F' = '678536fe-1083-478a-9c59-b99265e6b0d3'
'S' = '20d37865-089c-4dee-8c41-6967602d4ac8'
}
$selectedPermissionValue = $permissionMapping[$selectedPermission]
# Requires an admin
if ($TenantId)
{
Join-MgGraph -Scopes "Software.ReadWrite.All Person.Learn AppRoleAssignment.ReadWrite.All" -TenantId $TenantId
}
else
{
Join-MgGraph -Scopes "Software.ReadWrite.All Person.Learn AppRoleAssignment.ReadWrite.All"
}
# Graph permissions constants
$sharePointResourceId = "00000003-0000-0ff1-ce00-000000000000"
$SitePermission = @{
Id=$selectedPermissionValue
Kind="Position"
}
# Get context for entry to tenant ID
$context = Get-MgContext
# Load cert
$cert = New-Object System.Safety.Cryptography.X509Certificates.X509Certificate2($CertPath)
Write-Host -ForegroundColor Cyan "Certificates loaded"
# Create app registration
$appRegistration = New-MgApplication -DisplayName $AppName -SignInAudience "AzureADMyOrg" `
-Net @{ RedirectUris="http://localhost"; } `
-RequiredResourceAccess @{ ResourceAppId=$sharePointResourceId; ResourceAccess=$UserReadAll, $GroupReadAll, $SitePermission } `
-AdditionalProperties @{} -KeyCredentials @(@{ Kind="AsymmetricX509Cert"; Utilization="Confirm"; Key=$cert.RawData })
Write-Host -ForegroundColor Cyan "App registration created with app ID" $appRegistration.AppId
# Create corresponding service principal
$servicePrincipal= New-MgServicePrincipal -AppId $appRegistration.AppId -AdditionalProperties @{} | Out-Null
Write-Host -ForegroundColor Cyan "Service principal created"
Write-Host
Write-Host -ForegroundColor Inexperienced "Success"
Write-Host
# Offering admin consent
$scp = Get-MgServicePrincipal -Filter "DisplayName eq '$($AppName)'"
$app = Get-MgServicePrincipal -Filter "AppId eq '$sharePointResourceId'"
New-MgServicePrincipalAppRoleAssignment -ServicePrincipalId $scp.id -PrincipalId $scp.Id -ResourceId $app.Id -AppRoleId $selectedPermissionValue
# Generate Join-MgGraph command
$connectGraph = "Join-MgGraph -ClientId """ + $appRegistration.AppId + """ -TenantId """`
+ $context.TenantId + """ -CertificateName """ + $cert.SubjectName.Identify + """"
Write-Host $connectGraph
if ($StayConnected -eq $false)
{
Disconnect-MgGraph
Write-Host "Disconnected from Microsoft Graph"
}
else
{
Write-Host
Write-Host -ForegroundColor Yellow "The connection to Microsoft Graph remains to be lively. To disconnect, use Disconnect-MgGraph"
}
Save the file as RegisterAppOnly.ps1 and run the PowerShell script.
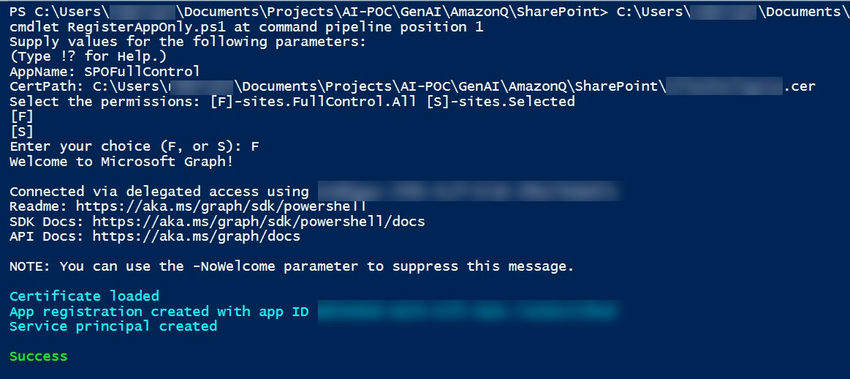
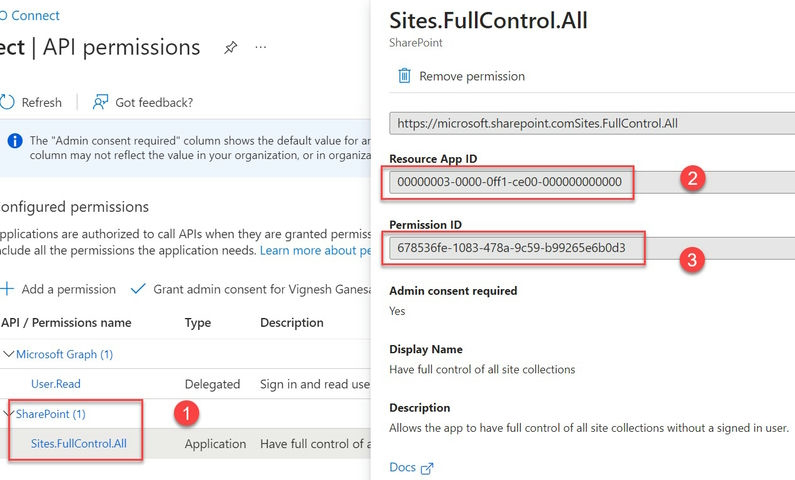
Be aware. SharePointResourceId and SitePermissionID are captured, as proven within the screenshot under.
Abstract
This text describes methods to register an app with Microsoft Entra ID and configure SharePoint permissions utilizing PowerShell.
Know extra about our firm at Skrots. Know extra about our companies at Skrots Companies, Additionally checkout all different blogs at Weblog at Skrots