Upgrading The IPsec/ IKE Coverage To The Azure Web site-To-Web site VPN Connection Utilizing The Azure Portal
Introduction
In our earlier article we realized the way to improve the IPsec/IKE coverage to the Azure Web site-to-Web site VPN Connection utilizing PowerShell. On this article, we’re going to learn to configure an IPsec/IKE coverage for site-to-site (S2S) VPN connections utilizing the Azure Portal.
Step 1
Earlier than upgrading the connection, please confirm that the next steps are configured within the Azure portal.
- Digital Community
- Gateway subnet
- VPN Gateway
- Native Community Gateway
- VPN connection
Step 2
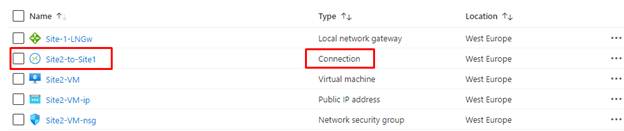
Within the Azure Portal, go to the right “Useful resource group” after which open the “VPN Connection”.
On this demo our Connection identify is “Site2-to-Site1”
Step 3
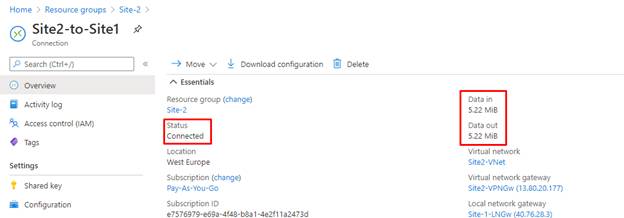
Be sure that the connection is up and working with any situation
Step 4
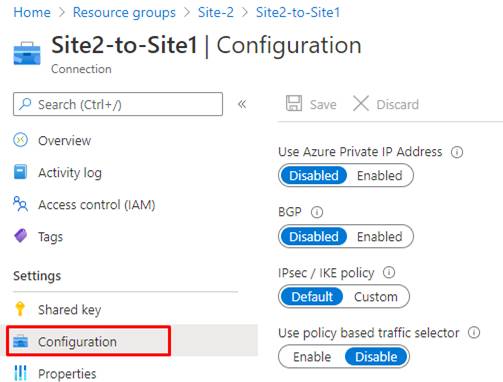
Go to the “Configuration” below the Settings.
Step 5
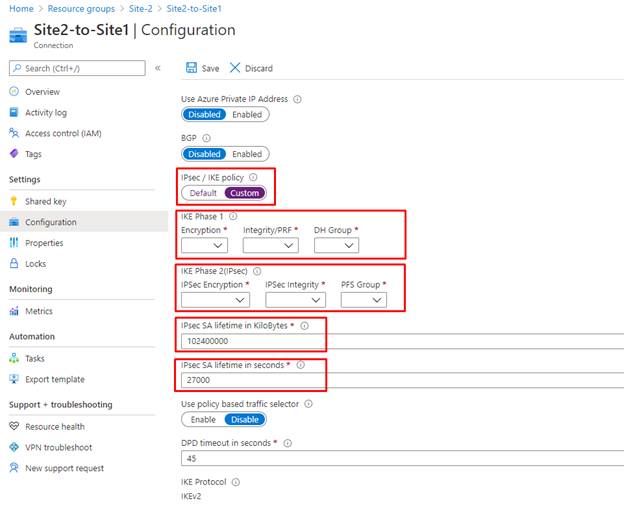
Configuration settings, choose the IPsec / IKE coverage to “Customized”, now we enter the IKE Section 1 and IKE Section 2 (IPsec) parameters.
Step 6
Now we’re going to enter the parameters for the IKE Section 1 and IKE Section 2 (IPsec). on this demo we’re going to enter the beneath parameters.
- IKE Section 1
- Encryption – AES256
- Integrity/PRF – SHA256
- DH Group – DHGroup2
- IKE Section 2 (IPsec)
- IPsec Encryption – AES256
- IPsec Integrity – SHA256
- PFS Group – PFS2
- IPsec SA lifetime in KiloBytes – 102400000
- IPsec SA lifetime in seconds – 28800
Step 7
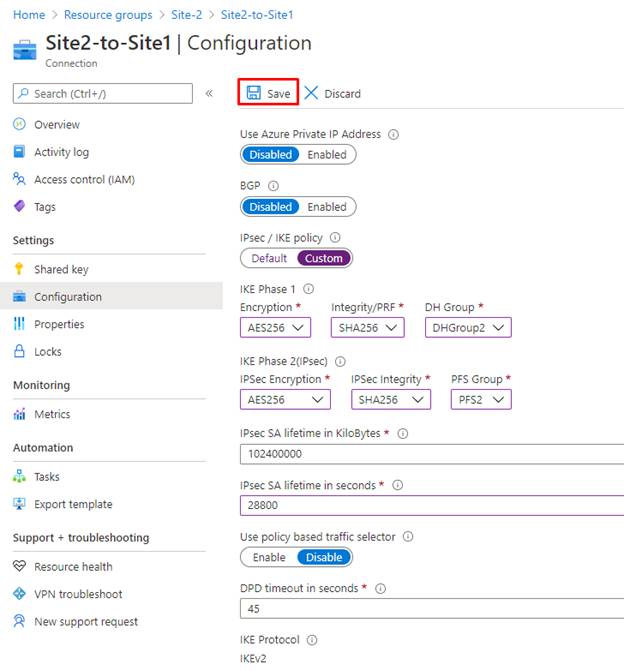
After getting into the parameters click on “Save”.
Observe
Coverage-based Visitors Selectors should not supported in Azure Stack Hub.
Vital
As soon as the IPsec/IKE coverage is upgraded to the connection, the Azure VPN gateway will solely ship or settle for the IPsec/IKE proposal with specified cryptographic algorithms and key strengths on that specific connection. Be sure that your on-premises VPN gadget for the connection makes use of or accepts the precise coverage mixture, in any other case the S2S VPN tunnel won’t set up.
Abstract
On this article, we now have realized the way to improve the VPN Connection parameters utilizing the Azure Portal. In our earlier article we realized to improve the VPN Connection parameters utilizing the PowerShell instructions. In case you have any questions be at liberty to contact me.