Highway To AZ-204 – Implement Person Authentication And Authorization
OAuth 2.Zero is an authorization framework, it gives an interface for third-party functions to acquire entry to protected HTTP sources.
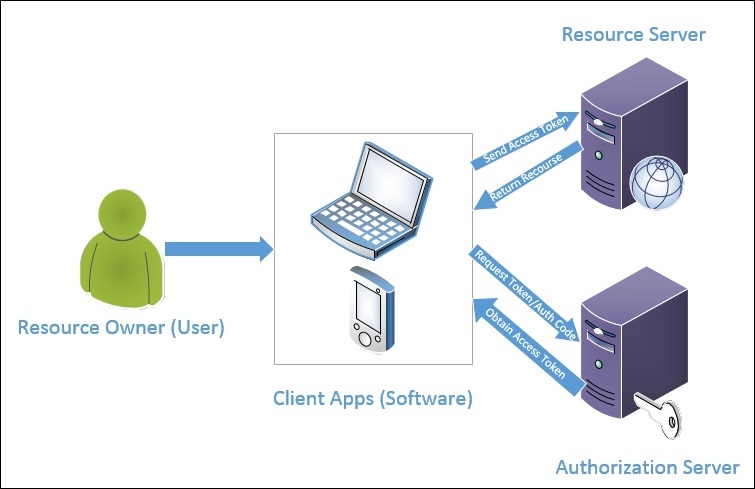
The OAuth 2.Zero framework is split into four primary items, as follows,
- Useful resource Proprietor, the place now we have customers. They’re distinctive recognized by their login;
- Consumer Apps, are the applying itself. They’re recognized by their distinctive consumer Id.
- Useful resource Server has endpoints protected which will solely be accessed after efficiently validating the token supplied by the Consumer App towards the Authorization Server;
- Authorization Server holds the logic to generate and validate tokens based mostly on the Useful resource Proprietor and Consumer Apps.
OAuth2 Scopes
Scopes are used to restrict the Useful resource Server’s entry to info by the Person. Consumer Apps might request entry to a large sort of scopes so as to carry out its operation whereas the person has to consent or not.
For instance of utilizing scopes, now we have cellular functions that ask consent to have entry to completely different sources on our telephone, just like the contact checklist, digital camera, audio, and so on.. Every a type of sources is a scope.
OAuth2 Consumer Varieties
OAuth 2.Zero helps two varieties of consumer sorts in response to their functionality to retailer credentials securely which is able to influence instantly on how they will learn the token, as follows,
- Confidential Consumer can retailer credentials securely. The token could be learn Symmetrically with the consumer secret or Asymmetrically with a personal key.
- Public Consumer, cannot retailer credentials securely. The token could be learn Asymmetrically with a personal key or with the general public key used to signal the personal key.
OAuth2 Grant Varieties
OAuth 2.Zero has a variety of grant sorts accessible so far as the chance to create customized ones however their most used grant sorts are as follows,
- Authorization Code is probably the most used grant sort whereas public and confidential shoppers alternate the authorization code for an entry token.
- Consumer Credentials, when the app sends its personal credentials (consumer id and consumer secret) so as to get hold of an entry token.
- Machine Code, utilized by gadgets to alternate a beforehand obtained machine code for an entry token;
- Refresh Token, used when the token is expired so the consumer exchanges the refresh token for a model new token with none interplay with the person.
OAuth2 Bearer Token
The Bearer token is probably the most used sort of token used with OAuth 2.0. It’s composed of the phrase Bearer adopted by the token, this token might vary from hexadecimal string to extra structured varieties of tokens.
Instance of utilization,
- Authorization: Bearer eyJhbGciOiJSUzI1NiIsastpZCI6IkM3MDQ2QjI0Mzc4RTJCNjYwMjI1MzFCNTcwQjY5NDNEREYyOEMwRDAiLCJ0eXAiOiJKV1QiLCJ4NXQiOiJ4d1JySkRlT0syWUNKVEcxY0xhVVBkOG93TkEifQ.eyJuYmsYiOjE2MDIyNTU1NDcsImV4cCI6MTYwMjI2OTk0NywiaXNzIjoiaHR0cHM6Ly9hdXRoLmFcuZXBlcmYuY29tIiwiYXVkIjpbImh0dHBzOi8vYXV0aC5hbmVwZXJmLmNvbS9yZXNvdXJjZXMiLCJld3BlbmV0d29ya2FwaSIsImV3cG
Microsoft Id Platform
Microsoft Id Platform works as an Authorization Server however is far stronger than any regular Authorization Server as a result of it has different functionalities reminiscent of passwordless authentication, step-up authentication, and conditional entry.
Microsoft Id Platform affords an interface to handle authorization amongst Azure sources, being able to assigning sources to entry different sources with out explicitly doing an authorization request.
It’s constructed by a number of parts so as to obtain its so highly effective engine as follows,
- OAuth2.Zero for authorizations;
- OpenId Join for authentications;
- Microsoft Authentication Library ( MSAL ) for authenticating customers towards the Microsoft Id platform;
- Azure Portal to handle and configure your functions, authorizations, and authentications;
What are Shared Entry Signatures – SAS?
Shared Entry Signatures handles authorization and authentication, they’re tokens generated with very particular functions to entry sources, these tokens might have limitations reminiscent of which useful resource it could entry, which operations (learn, write, delete) could also be executed and through which era vary it may be used. Shared Entry Signatures are grouped in three differing types as follows,
- Person delegation SAS utilized for Blob Storages solely and combines the safety of the Azure AD with the permissions from the SAS;
- Service SAS, utilized at Blob storage stage, Queue storage stage, Desk storage stage, or Azure Information stage. May be assigned with a Saved Entry Coverage;
- Account SAS utilized on the Storage Account stage and cannot be used with a Saved Entry Coverage;
Saved Entry Coverage with SAS
Saved Entry Insurance policies are insurance policies, on the container stage, related to a number of SAS which defines constraints for these related SAS.
It’s a good observe to affiliate SAS with Saved Entry Coverage as a result of when a SAS is related to a Saved Entry Coverage this SAS inherits all of the constraints from the Saved Entry Coverage, and if that you must revoke entry for this SAS you solely must terminate the entry from the Saved Entry Coverage as an alternative of needing to generate a brand new storage account key. By producing a brand new storage account key you would need to replace your shoppers to make use of the brand new key so as to entry its sources.
These constraints are those as follows,
- Begin time, the date that the Saved Entry Coverage will begin to be legitimate. SAS related to this Saved Entry Coverage cannot be used earlier than the beginning time.
- Finish time, the date that the Saved Entry Coverage will expire. These SAS related to this Saved Entry Insurance policies goes to run out collectively.
- Permissions, the sources, and operations that this Saved Entry Coverage will be capable of manipulate.
What are Function-Based mostly Entry Controls (RBAC)?
Azure Function-Based mostly Entry Controls is one other safety performance that helps the way you handle entry via your sources. It handles customers’ authorization, managing who has entry to every useful resource, and what every person can do with every useful resource.
To be able to perceive higher find out how to Azure Function-Based mostly Entry Controls works let’s undergo its key ideas, as follows,
- Safety Principal, an object that represents a person, group, service principal, or managed id who’s request entry to an Azure useful resource. Roles are assigned to Safety Principals;
- Function Definition, assortment of permissions with an inventory of operations that could be executed by every permission;
- Scope, holding entry for every function. Scopes could be configured at a administration group, subscription, useful resource group, or useful resource ranges;
- Function Project, which is the method of assigning a job to a safety principal;
- A number of Assignments occurs when you may have multiple function assigned to the identical safety principal to the identical useful resource. When it occurs, Azure sums the roles with out influence any of them;
- Deny Project, is the other of the Function Project whereas we specify a set of actions which might be denied.
To arrange these roles, Azure distributes the managing amongst some varieties of customized roles and pre-created roles, the pre-created roles are those as follows,
- Subscription Administrator Roles, having full entry to the subscription account and is grouped in three subcategories as follows
- Account Administrator, 1 per Azure Account and manages primarily the billing;
- Service Administrator, 1 per Azure Subscription and manages the providers within the Azure Portal;
- Co-Administrator, 200 per subscription and has the identical privileges because the Service Administrator;
- Azure Roles, offering entry administration to Azure sources. Some sources have their particular roles however there are some basic roles utilized to all sources as follows:
- Proprietor, full entry to all sources and might delegate entry to others;
- Contributor, full entry to all sources;
- Reader, studying sources however not with the ability to replace/delete/create it;
- Person Entry Administrator, managing customers’ entry to Azure sources;
- Azure AD Roles used to handle Azure AD sources and is grouped in three primary classes as follows:
- World Administrator manages entry to Azure AD Sources and assign the Person Administrator function to others;
- Person Administrator manages entry to customers and teams. Additionally, manages tickets and well being;
- Billing Administrator, managing the billing of the account;
What’s Azure AD?
Azure Energetic Listing is Microsoft’s cloud-based id that handles Authorization and Authentication for inside(Azure, Microsoft 365, and so on..) and exterior sources (your organization intranet, company community, and so on..), certainly one of its primary options is to entry a variety of Functions and Techniques inside a Single Signal-On.
Inside Azure AD you possibly can handle all of your customers and apps in a single location, which signifies that your customers might change from one app to a different while not having to log in once more, with out risking safety. Really, your safety goes via an enormous enhance so far as your customers is not going to must retailer and enter completely different usernames and passwords when they’re accessing completely different apps, and Azure AD additionally affords multi-factor authentication, which might be serving to you and your group with governance and a better layer of safety.
To be able to perceive higher about Azure AD, we’re going via a quick rationalization of its primary terminologies as follows,
- Id might be a person, an software, and even one other server that should get authenticated;
- Account, an id with associated knowledge;
- Azure AD Account, an id created via Azure AD or one other Microsoft cloud service;
- Azure Tenant represents a single group inside Azure AD;
- Single Tenant APPs, apps that belong to a single Azure Tenant;
- Multi-Tenant APPs, apps that belong to multiple Azure Tenant;
- Azure AD listing, the devoted Azure AD listing owned by the tenant. It has customers, teams, and apps;
- Customized Area, domains now owned by Microsoft;
- MSA, the Microsoft Account (Outlook, Xbox Stay, Workplace 365 accounts) ;
Sensible Examples
OAuth2 Authentication