Monitor The Azure Lively Listing Consumer Secret Expiration
Each time an utility is stay it’s necessary to stick with it and working with out downtime. However what in case your utility stops abruptly simply since you overlook to replace the expired ClientSecrets? It will have an effect on your prospects and enterprise and you’re going to get lot of escalation emails. Being an utility proprietor, you don’t need your utility to have Software Downtime.
To keep away from all these let’s implement a PowerShell script with assist of Azure Operate to observe the expiration of your Azure AD app consumer secrets and techniques and ship an e mail to the respective customers prematurely earlier than it expires.
I hope you’re you’re already conscious of beneath applied sciences which is required for this implementation, if not please take a look at every official documentation.
Create Azure Timer Set off
- Login to Azure Portal
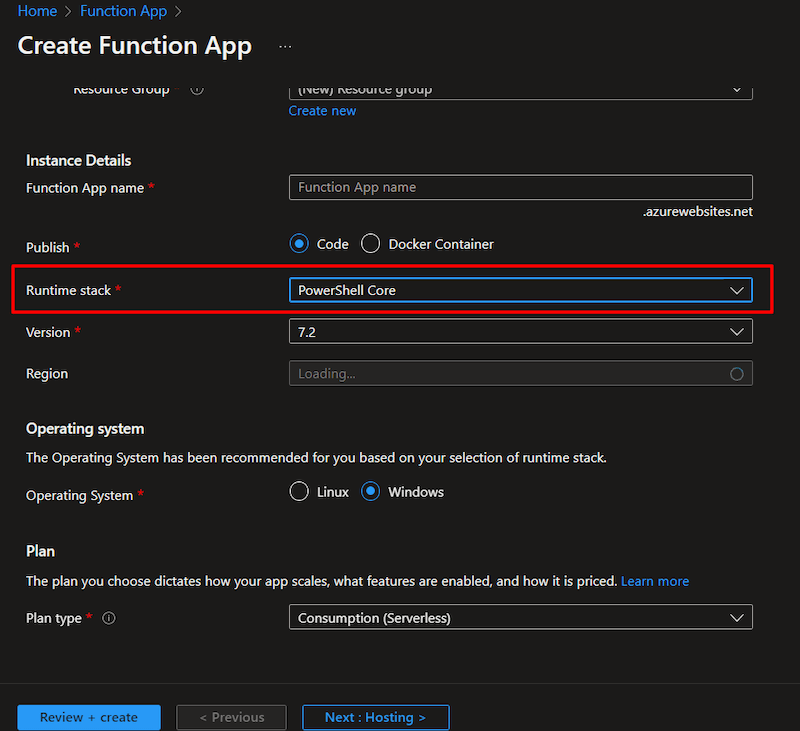
- Seek for Azure Operate App and create the useful resource with required particulars.
- Guarantee to decide on the Operate runtime as PowerShell Core
- As soon as the useful resource received created, go to the Capabilities menu within the left pane and click on “Create Set off” then select “Timer Set off”
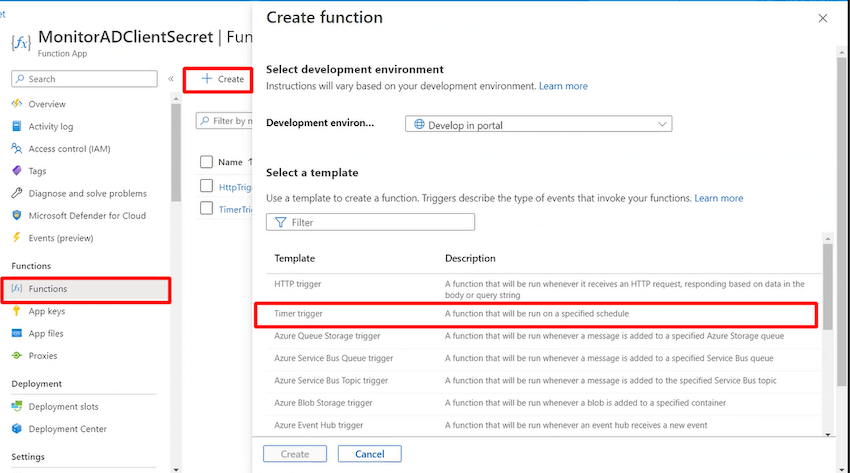
The right way to change the schedule in Timer Set off
- Timer triggers are based mostly on schedules, if you wish to change the time when the set off ought to occur.
- Click on in your operate title and within the upcoming display screen go to “Code + Take a look at” menu.
- Choose operate.json from the information dropdown and search for the “schedule” object within the json to vary the schedule timing.
- Be taught extra in regards to the which expressions to make use of for the timing, please take a look at NCRONTAB expressions
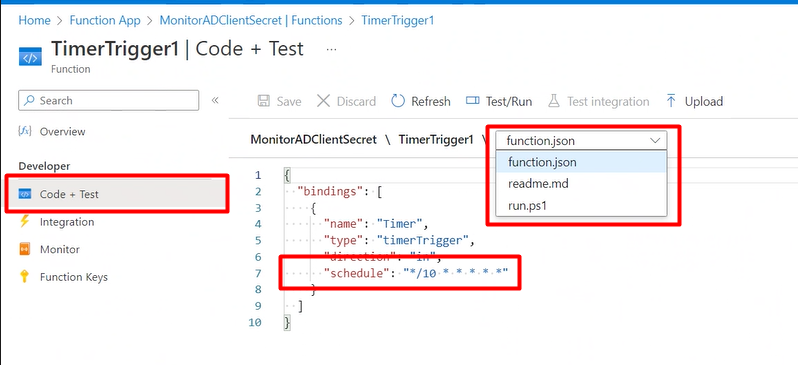
The right way to allow AZ PowerShell module in Azure Capabilities
Azure capabilities by default help AZ module to carry out operations in Azure Sources. Under are the steps to allow it.
Take a look at Azure PowerShell module instructions to study extra about it.
- Go to your Operate App and within the left pane click on App Recordsdata.
- Choose “necessities.psd1” from the information dropdown and uncomment the Az module because the beneath display screen shot. Should you needed particular Az module model additionally you may modify it.
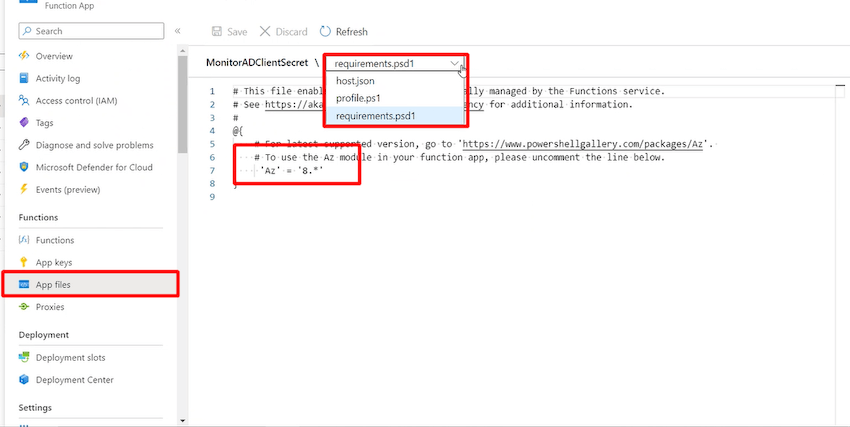
Enabling Managed Identification in Azure Capabilities
We would want to allow Managed identification to grant permission to our Azure Operate app to entry the Lively Listing. Please check out use managed identities for App Service and Azure Capabilities to allow it.
The right way to assign Software administrator permission to Azure Managed identification
- Go to Azure Lively Listing and within the touchdown, web page choose “Roles and directors”
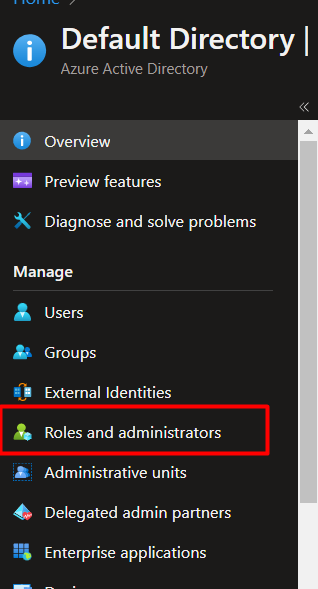
- Within the upcoming display screen, choose “Software administrator” after which click on “Add Assignments”.
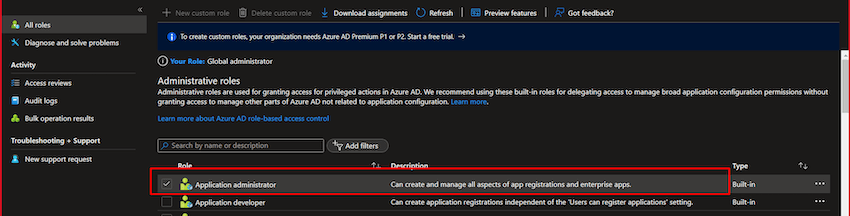
- Then search your managed identification and grant the permission. After granting permission you will discover your Azure operate app identification below assignments as beneath,
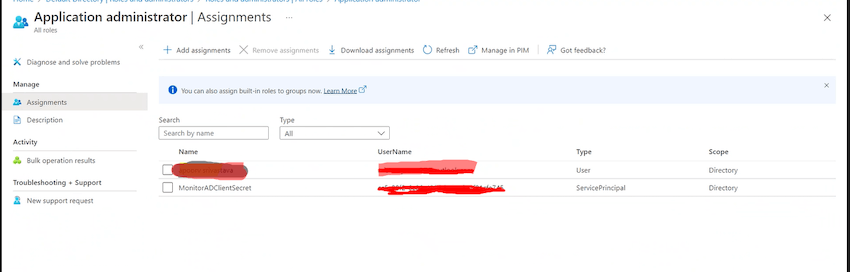
Now all of the perquisites and the setup finished for our implementation let’s see the precise script to do this,
PowerShell Code in Azure Operate to observe Azure AD Consumer Secrets and techniques
- Add the expiration days to observe and Webhook submit hyperlink in Operate App configuration as beneath, so it may be accessed within the operate code.
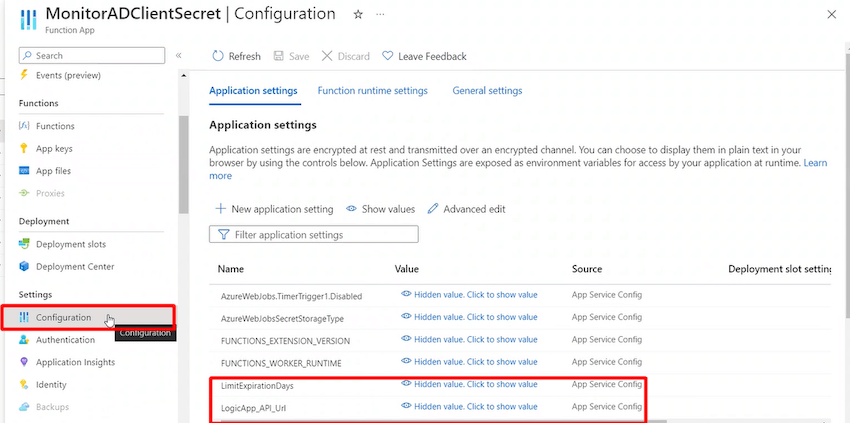
- Now our script will learn all of the AD apps for which consumer secrets and techniques will expire earlier than the configured timeframe and fetch the meta particulars like Description, ExpiryDate, AppID, AppObjectID, AppName and Key Identifier.
- Even when there are a couple of consumer secrets and techniques are expiring in the identical Azure AD app. It can even be returned as a separate object within the ensuing array.
- The previous few strains of the code will submit the Array object to WebHook.
- Right here is the total code go to your Timer Set off Operate and click on “Code + Take a look at” and change the code editor with beneath code
# Enter bindings are handed in through param block. param($Timer) #secret expiration date filter (for instance 30 days) $LimitExpirationDays = $env:LimitExpirationDays $SecretsToExpire =@() #Retrieving the listing of secrets and techniques that expires within the above vary of days Get-AzADApplication | ForEach-Object { $app = $_ @( Get-AzADAppCredential -ObjectId $_.Id ) | The place-Object { $_.EndDateTime -lt (Get-Date).AddDays($LimitExpirationDays) } | ForEach-Object { $expiringSecret = @{ AppName = $app.DisplayName AppObjectID = $app.Id AppApplicationId = $app.AppId SecretDisplayName = $_.DisplayName SecretKeyIdentifier = $_.KeyId SecretEndDate = $_.EndDateTime } $SecretsToExpire += $expiringSecret } } #Printing the listing of secrets and techniques which might be close to to run out if($SecretsToExpire.Rely -EQ 0) { Write-Output "No secrets and techniques discovered that can expire on this vary" } else { Write-Output "Secrets and techniques that can expire on this vary:" Write-Output $SecretsToExpire.Size Write-Output $SecretsToExpire | ConvertTo-Json $headers = @{ 'Content material-Sort' = 'utility/json' } if($SecretsToExpire.Size -EQ 1){ Invoke-RestMethod -Methodology 'Publish' -Headers $headers -Uri $env:LogicApp_API_Url -Physique (ConvertTo-Json @($SecretsToExpire)) } else ConvertTo-Json) }
Now the subsequent step is to ship notification to the consumer, it may be any form of webhook/API URL which obtain your POST name from PowerShell and course of the Request knowledge to ship emails. You can also make this course of simpler whenever you go together with Azure Logic Apps because it has default connectors for Mailing.
Now our eyes are on the expiring Consumer Secrets and techniques earlier than it expires which screens it on every day foundation.
Word: Should you don’t wish to obtain the emails or run the set off, go to your Timer Set off -> Overview web page and Disable the Operate quickly.