How To Create Your Personal Azure Customized Coverage
Introduction
Earlier than creating Azure customized insurance policies, I wish to clarify a little bit of background relating to the insurance policies. It’s an integral a part of Azure governance so right here the query comes what governance is. Azure governance is identical like the opposite governance principals utilized by our authorities and all of the group these needed to implement their very own insurance policies within the group with a view to be compliant. These days we have now additionally heard in regards to the phrase “GDPR” that is additionally the kind of governance that has been imposed globally and it’s associated to private information safety insurance policies, so organizations which might be coping with any sort of private information have to be compliant with this.
We talked an excessive amount of about governance, let’s come again to the Azure insurance policies, these are the insurance policies that may be carried out by the organizations on Azure subscriptions or administration group stage with a view to safe the surroundings, which means by way of Azure insurance policies we will management the conduct of useful resource provisioning in Azure. Sources with undesired configuration might be denied by the coverage or an extra useful resource/service might be deployed/audited by the coverage. Some use circumstances for Azure coverage embrace implementing governance for useful resource consistency, regulatory compliance, safety, value, and administration.
For e.g. suppose an XYZ group that’s working solely in Asia pacific and does not wish to present the sources within the US area. So by utilizing an Azure coverage we will limit this conduct.
Forms of insurance policies
Mainly, there are two sorts of insurance policies accessible in Azure,
- Constructed-in
These are pre-inbuilt insurance policies which might be supplied by Microsoft and can be utilized as it’s in keeping with the requirement however can’t be altered. - Customized
These insurance policies might be created by personal as per our requirement and customised accordingly, right here I’ll clarify how you can create a customized coverage.
Sort of Results
As everyone knows and its title suggests, a coverage is principally a sort of rule that has some impact if that exact rule is carried out. In the identical approach, the Azure coverage additionally comprises a Rule and Impact of that Rule after assigned.
There are some widespread results that can be utilized whereas creation of a customized coverage in Azure.
Deny
Deny Useful resource creation if the checked situation is true
Audit
Useful resource creation will not be denied however an alert will present the non-compliance of the useful resource
AuditIfNotExists
If the present situation is true, useful resource compliant; if not, useful resource non-compliant. Useful resource creation will not be blocked
DeployIfNotExists
If the present situation is true, no impact, no deployment; if the existence situation is fake, impact activated, deployment of a proper configuration or of a sub-resource.
Results Categorization
- Detection Results – Audit , auditIfnotExists
- Prevention Results – Deny
- Remediation results – DeployIfnotExists
A coverage might be carried out and deployed in two elements,
- Create the coverage definition
- Assign the definition to a subscription/administration group.
Let’s have a look at how a customized coverage might be created utilizing the Azure portal.
Steps
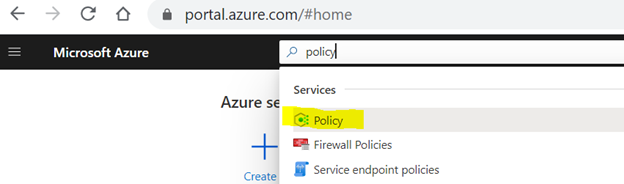
- Go to the portal and seek for “Coverage” within the market then click on on highlighted service.
- Click on on “definitions”.
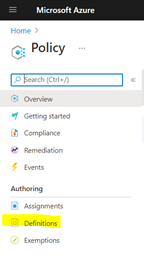
- Click on on +Coverage definition.
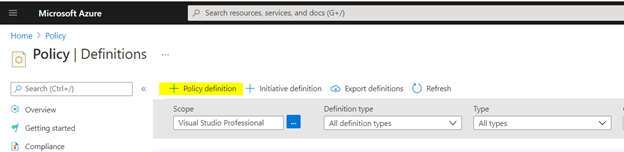
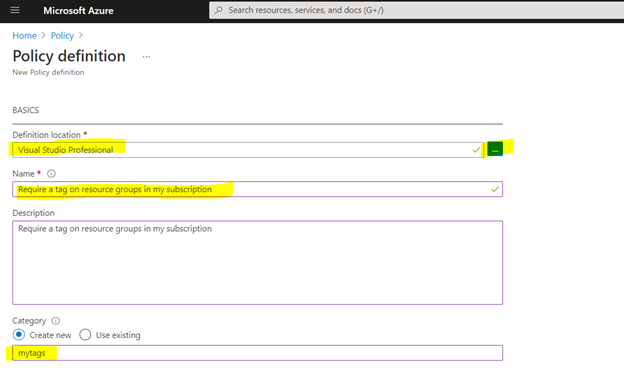
- You possibly can select “definition location” both your subscription/administration group and definition title, description, coverage rule, after which click on on “Save”.
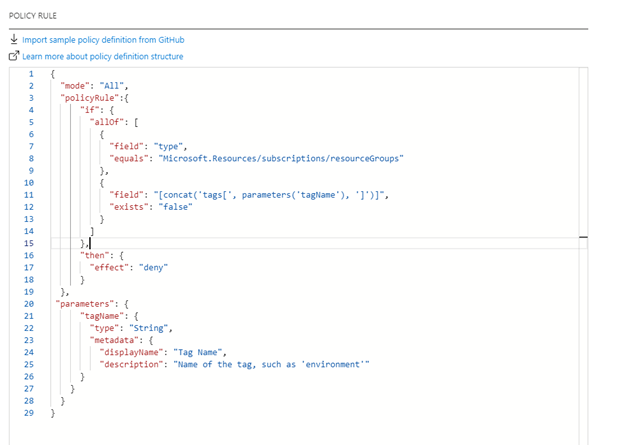
- {
- “mode”: “All”,
- “policyRule”: {
- “if”: {
- “allOf”: [
- {
- “field”: “type”,
- “equals”: “Microsoft.Resources/subscriptions/resourceGroups”
- },
- {
- “field”: “[concat(‘tags[‘, parameters(‘tagName’), ‘]’)]”,
- “exists”: “false”
- }
- ]
- },
- “then”: {
- “impact”: “deny”
- }
- },
- “parameters”: {
- “tagName”: {
- “kind”: “String”,
- “metadata”: {
- “displayName”: “Tag Title”,
- “description”: “Title of the tag, such as ‘surroundings'”
- }
- }
- }
- }
Conclusion
We’ve efficiently created a customized coverage in Azure with Deny impact and are in a position to validate the impact in motion. It’s simple to create these insurance policies and safe the surroundings towards undesired configuration useful resource creation. It really works nicely in massive organizations which have lots of subscriptions to handle the useful resource and governance.