Azure Container Registry: Mitigating knowledge exfiltration with devoted knowledge endpoints
Azure Container Registry pronounces devoted knowledge endpoints, enabling tightly scoped shopper firewall guidelines to particular registries, minimizing knowledge exfiltration considerations.
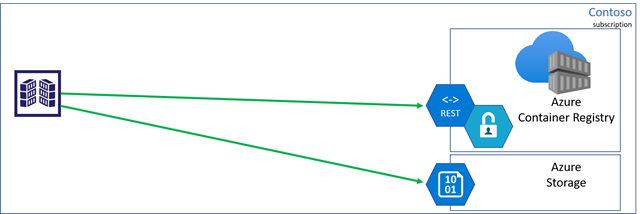
Pulling content material from a registry includes two endpoints:
- Registry endpoint, also known as the login URL, used for authentication and content material discovery.
A command likedocker pull contoso.azurecr.io/hello-worldmakes a REST request which authenticates and negotiates the layers which signify the requested artifact. - Information endpoints serve blobs representing content material layers.
Registry managed storage accounts
Azure Container Registry is a multi-tenant service, the place the info endpoint storage accounts are managed by the registry service. There are numerous advantages for managed storage, akin to load balancing, contentious content material splitting, a number of copies for greater concurrent content material supply, and multi-region help with geo-replication.
Azure Personal Hyperlink digital community help
Azure Container Registry just lately introduced Personal Hyperlink help, enabling personal endpoints from Azure Digital Networks to be positioned on the managed registry service. On this case, each the registry and knowledge endpoints are accessible from inside the digital community, utilizing personal IPs.
The general public endpoint can then be eliminated, securing the managed registry and storage accounts to entry from inside the digital community.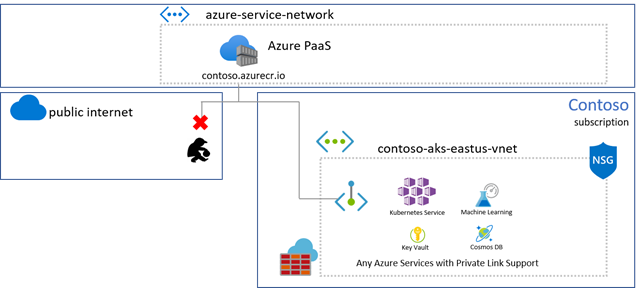
Sadly, digital community connectivity isn’t all the time an possibility.
Shopper firewall guidelines and knowledge exfiltration dangers
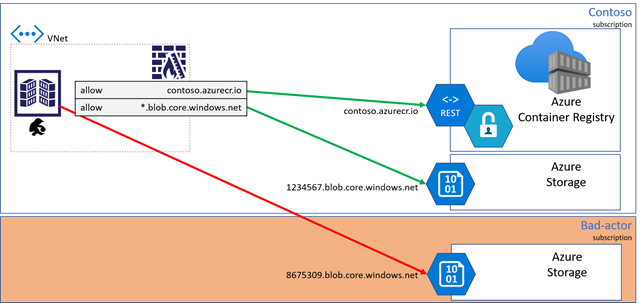
When connecting to a registry from on-prem hosts, IoT units, customized construct brokers, or when Personal Hyperlink is probably not an possibility, shopper firewall guidelines could also be utilized, limiting entry to particular assets.
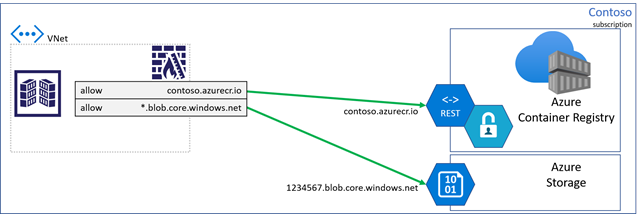
As prospects locked down their shopper firewall configurations, they realized they need to create a rule with a wildcard for all storage accounts, elevating considerations for data-exfiltration. A foul actor might deploy code that may be able to writing to their storage account.
To mitigate data-exfiltration considerations, Azure Container Registry is making devoted knowledge endpoints accessible.
Devoted knowledge endpoints
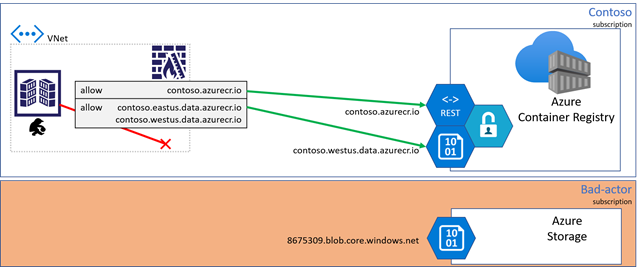
When devoted knowledge endpoints are enabled, layers are retrieved from the Azure Container Registry service, with totally certified domains representing the registry area. As any registry could turn into geo-replicated, a regional sample is used:
[registry].[region].knowledge.azurecr.io.
For the Contoso instance, a number of regional knowledge endpoints are added supporting the native area with a close-by duplicate.
With devoted knowledge endpoints, the dangerous actor is blocked from writing to different storage accounts.
Enabling devoted knowledge endpoints
Word: Switching to devoted data-endpoints will influence shoppers which have configured firewall entry to the prevailing *.blob.core.home windows.web endpoints, inflicting pull failures. To guarantee shoppers have constant entry, add the brand new data-endpoints to the shopper firewall guidelines. As soon as accomplished, present registries can allow devoted data-endpoints via the az cli.
Utilizing az cli model 2.4.zero or higher, run the az acr replace command:
az acr replace --name contoso --data-endpoint-enabled
To view the info endpoints, together with regional endpoints for geo-replicated registries, use the az acr show-endpoints cli:
az acr show-endpoints --name contoso
outputs:
{
"loginServer": "contoso.azurecr.io",
"dataEndpoints": [
{
"region": "eastus",
"endpoint": "contoso.eastus.data.azurecr.io",
},
{
"region": "westus",
"endpoint": "contoso.westus.data.azurecr.io",
}
]
}
Safety with Azure Personal Hyperlink
Azure Personal Hyperlink is probably the most safe method to management community entry between shoppers and the registry as community visitors is restricted to the Azure Digital Community, utilizing personal IPs. When Personal Hyperlink isn’t an possibility, devoted knowledge endpoints can present safe data in what assets are accessible from every shopper.
Pricing data
Devoted knowledge endpoints are a function of premium registries.
For extra data on devoted knowledge endpoints, see the pricing data right here.