Azure DevOps – Automate Bulk IP Tackle Restriction Of Azure App Service
This text is split into three components,
- Azure DevOps – Entry Restriction of Azure App Service utilizing Azure Administration Portal – We discovered how you can prohibit entry to the Azure App Service manually utilizing the Azure Portal.
- Azure DevOps – Bulk IP Tackle Restriction of Azure App Service dynamically utilizing PowerShell – We discovered how you can leverage PowerShell scripting to dynamically do bulk insertion of IP Addresses for configuring entry restrictions for the Azure App Service.
- Azure DevOps – Automate Bulk IP Tackle Restriction of Azure App Service dynamically utilizing PowerShell & Azure DevOps Pipeline – We are going to learn to automate the method of Entry Restriction each time there’s a change within the listing of IP addresses utilizing Azure DevOps Pipelines.
Azure DevOps – Automate Bulk IP Tackle Restriction of Azure App Service dynamically utilizing PowerShell & Azure DevOps Pipeline – All Strategies
Stipulations
- Azure Subscription
- Azure DevOps Account
- Azure App Service
Please be certain that an App Service is created.
Introduction
Within the earlier articles, Azure DevOps – Entry Restriction of Azure App Service utilizing Azure Administration Portal we’ve got discovered how you can manually add an Enable or Deny rule utilizing the Azure Administration Portal within the Networking / Entry Restrictions blade by offering the beneath info.
And, we’ve got additionally discovered how you can do Azure DevOps – Bulk IP Tackle Restriction of Azure App Service dynamically utilizing PowerShell.
It doesn’t make sense to run the PowerShell script manually each time there are new IP Addresses that should be added.
So, on this article, we’re going to learn to robotically execute the PowerShell script from the Azure DevOps pipeline.
Let’s add each the beneath recordsdata to a Repository as proven beneath,
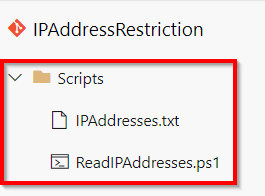
Azure DevOps – Automate Bulk IP Tackle Restriction of Azure App Service dynamically utilizing PowerShell & Azure DevOps Pipeline – Repository
Beneath is how the IPAddresses.txt recordsdata look with dummy IP Addresses.
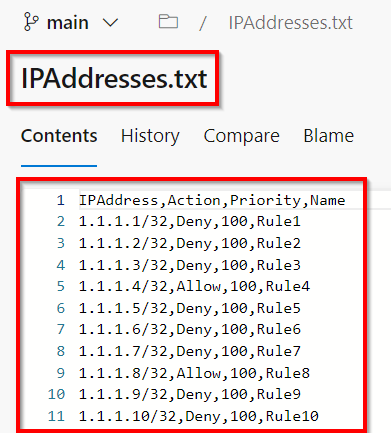
Azure DevOps – Automate Bulk IP Tackle Restriction of Azure App Service dynamically utilizing PowerShell & Azure DevOps Pipeline – Dummy IP Tackle
Let’s perceive the subsequent steps.
Construct Pipeline
Within the construct pipeline, we are going to solely be including the PowerShell script file (ReadIPAddresses.ps1) and the IP Tackle file (IPAddresses.txt) into the bundle.
Launch Pipeline
Within the Launch pipeline, we are going to run the PowerShell script which provides the IP Tackle restrictions to the App Service – Internet App.
Let’s begin engaged on the pipelines.
Package deal the recordsdata utilizing Construct Pipeline
Packaging the recordsdata is once more a 2-step course of.
Step 1
Obtain the recordsdata from the git repository to the agent – As proven within the beneath screenshot, this step copies all of the contents ( * means all recordsdata) from the folder names Scripts right into a pre-defined location specified within the Construct.ArtifactStagingDirectory location inside the agent.
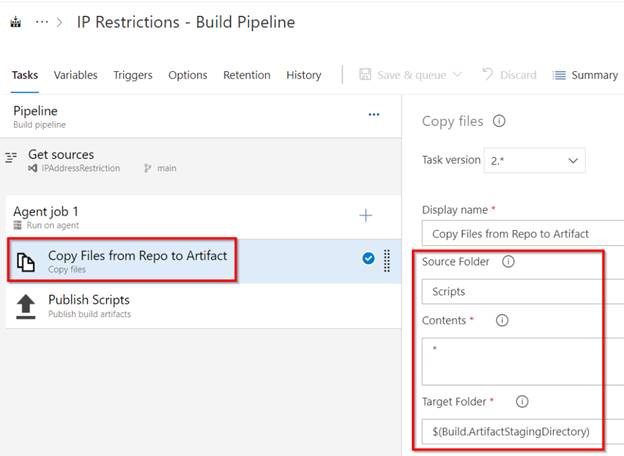
Azure DevOps – Automate Bulk IP Tackle Restriction of Azure App Service dynamically utilizing PowerShell & Azure DevOps Pipeline – Copy Artifacts
Step 2
Publish the Artifactory into the Azure Pipeline – as proven within the beneath screenshot, this step will publish (add) the artifacts from Construct.ArtifactStagingDirectory location to Azure Pipelines.
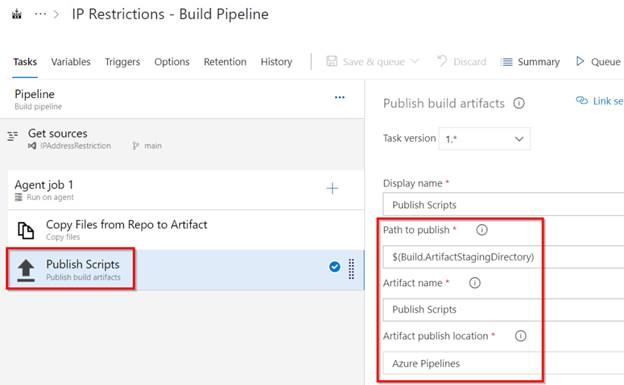
Azure DevOps – Automate Bulk IP Tackle Restriction of Azure App Service dynamically utilizing PowerShell & Azure DevOps Pipeline – Publish Artifacts
Go forward and run the pipeline. It’s best to see the beneath,
Within the Construct Pipeline execution abstract display, click on on the Artifacts hyperlink to view the revealed artifacts.
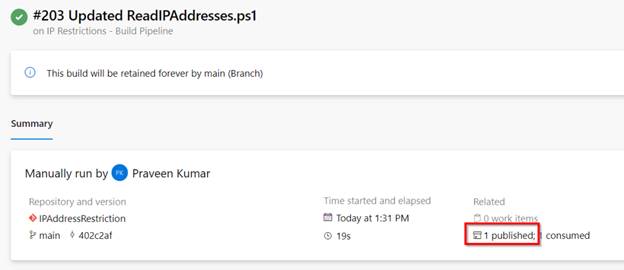
Azure DevOps – Automate Bulk IP Tackle Restriction of Azure App Service dynamically utilizing PowerShell & Azure DevOps Pipeline – Abstract
You can be taken to the beneath display the place you may see the recordsdata packaged.
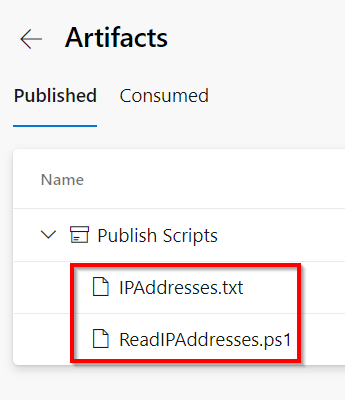
Azure DevOps – Automate Bulk IP Tackle Restriction of Azure App Service dynamically utilizing PowerShell & Azure DevOps Pipeline – Abstract – Publish Artifacts
The above screenshots show that the construct pipeline is profitable.
Execute the PowerShell with Launch Pipeline
On this part, we are going to learn to execute the PowerShell script. Let’s create a launch pipeline and add an Azure PowerShell job as proven beneath.
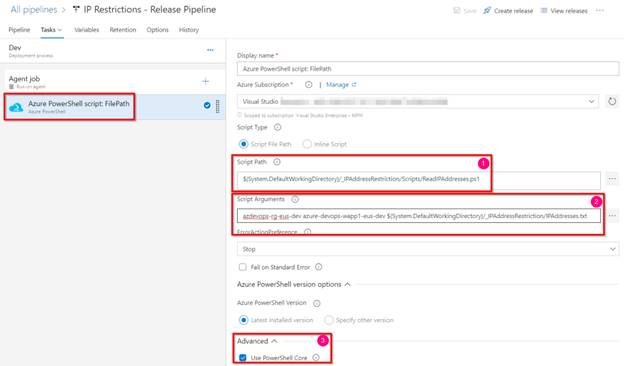
Azure DevOps – Automate Bulk IP Tackle Restriction of Azure App Service dynamically utilizing PowerShell & Azure DevOps Pipeline – Azure Energy shell – Cross Parameters
- Select the file which incorporates the PowerShell script
- Present the arguments to the PowerShell Script.
- Useful resource Group Identify
- App Service Internet App identify
- Location of the file which incorporates the IP Tackle listing
- Be sure that to decide on if you’re utilizing PowerShell core.
Lastly, after you run the pipeline, all of the IP Addresses will likely be added to the Entry Restrictions blade as proven beneath.
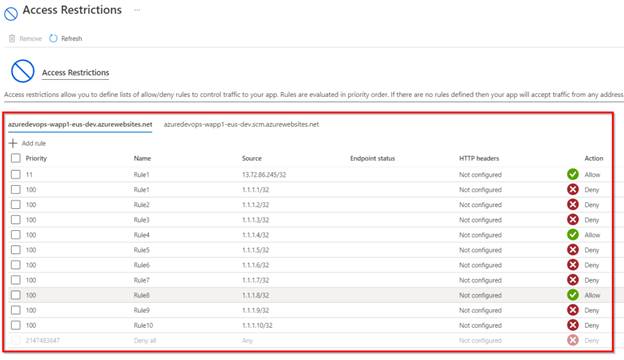
Azure DevOps – Bulk IP Tackle Restriction of Azure App Service dynamically utilizing PowerShell – Closing Entry Restrictions
That’s it. Now we have discovered how you can add the foundations utilizing PowerShell by integrating it with Azure DevOps pipelines.