Azure AD Privileged Id Administration
Introduction
Azure AD privileged id administration (AD PIM) service is used to manage entry permissions for privileged customers. This service supplies time-based and approval-based function activation to mitigate the dangers of extreme, pointless, or misused entry permissions on assets.
Why ought to we use this service and when it’s helpful?
Let’s contemplate you’re a international administrator and in your division, a consumer has privilege entry onto varied Azure assets like Azure SQL database or storage account and customers can do something with these assets i.e. type of excessive degree of privilege.
Now as an instance after a month or two, this consumer strikes out from this division. Now international administrator’s duty to make sure that all of the permissions of that consumer are revoked.
Generally when the variety of customers begins rising into the division, eradicating the consumer privilege hardly ever will get applied. Giving permissions to customers may be very simple however typically the administrator may neglect to take away the permissions for the unauthorized customers.
On this state of affairs, we will make use of Azure AD privilege id administration.
Utilizing this service, we will present time-based and approval-based function activation to the consumer.
The eligible consumer goes forward and takes an elevated function that could possibly be used to entry both assets in Azure otherwise you as a world administrator may additionally use Azure AD privilege id administration to permit customers to assign roles in Azure AD.
Key options of Privileged Id Administration
As an alternative of truly offering onetime full entry onto Azure AD or Azure assets, you’ll be able to present it simply in time entry through the use of Azure Privileged Id administration.
- We are able to assign time-bound entry to assets utilizing begin and finish dates. You too can make sure that approval is required to activate any of those privileged roles.
- We are able to implement multi-factor authentication to activate any function.
- We are able to additionally make sure that you get a notification when privilege roles are activated.
- We are able to conduct entry opinions to make sure customers nonetheless require the roles.
Implementing Azure AD PIM for Azure Assets
To allow Privileged Id administration for Azure Recourses, it is advisable first log in because the International Administrator for the listing. You need to have Azure AD Premium P2 licenses to make use of of PIM.
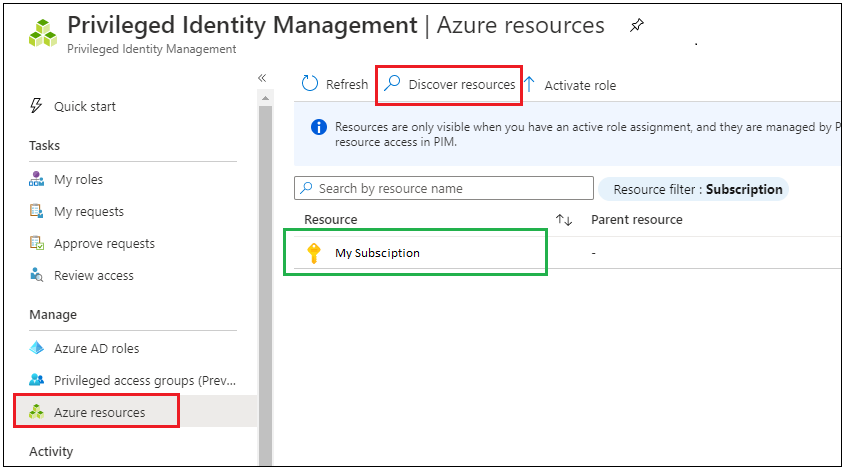
Seek for Privileged Id Administration in Azure Portal => Then go to Azure assets.
First, we have to uncover the assets as a part of your completely different subscriptions. Click on on “Discovery assets” => select your subscription => click on on “managed useful resource”.
Now return to Azure assets and you’ll see your subscription in place. Now we’re able to handle these assets by PIM.
Modify Position Settings of your Subscription (Non-compulsory)
Now go onto the subscription. For those who click on on the function part, these are role-based entry management and all the roles that may be assigned to customers to authorize the usage of assets which might be a part of your Azure subscription.
If you wish to modify function settings of one of many roles (let’s say Storage Account Contributor), go to Settings and alter the function setting for the Storage Account Contributor.
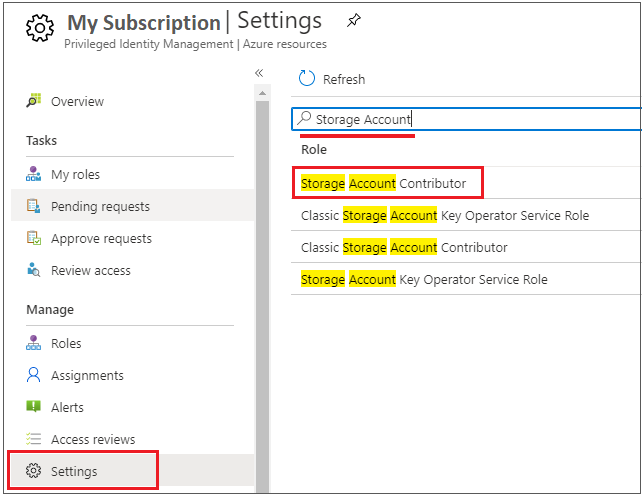
Now edit the function settings of Storage Account Contributor Position. Modify and replace the setting primarily based in your want for Activation/Task.
Within the Activation tab, there’s a most length possibility. So this function will solely be energetic for a length of eight hours. That implies that customers can now take up this function and that will be solely eligible for a length of eight hours.
Within the Task tab, I’m not permitting for everlasting eligible project and proscribing entry to activate inside three months solely.
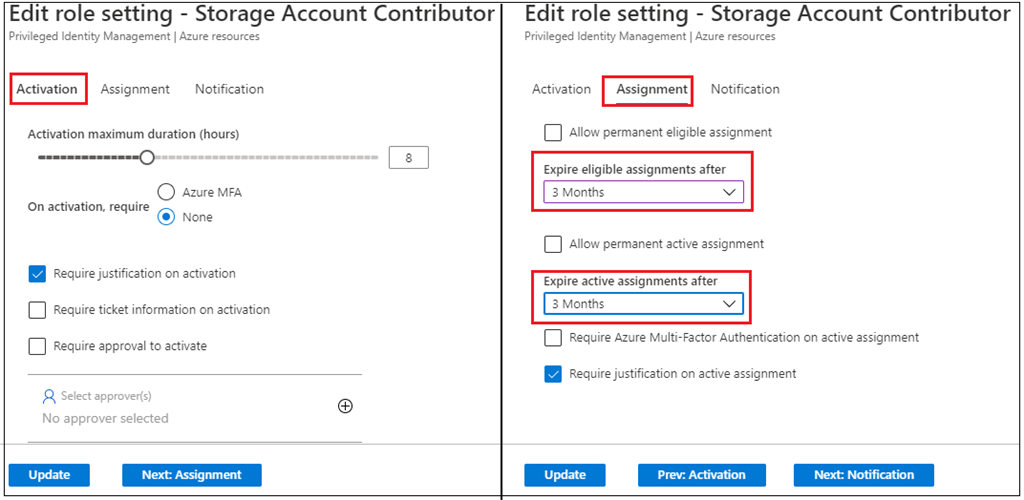
To this point we’ve got modified one of many RBAC function known as “Storage Account Contributor” and never permitting everlasting eligible project.
Assigning Position to Person
Now we are going to assign this function to a consumer.
First, go to Roles and seek for the Storage Account Contributor function. Choose that function and click on on Add assignments.
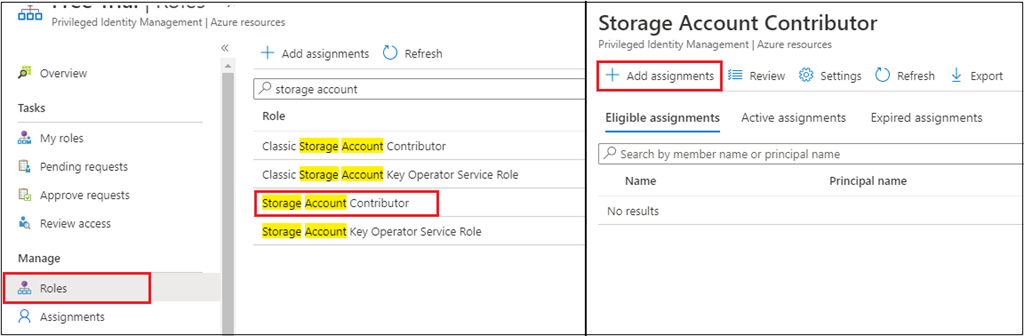
On Add Task display screen, choose a member to assign the function.
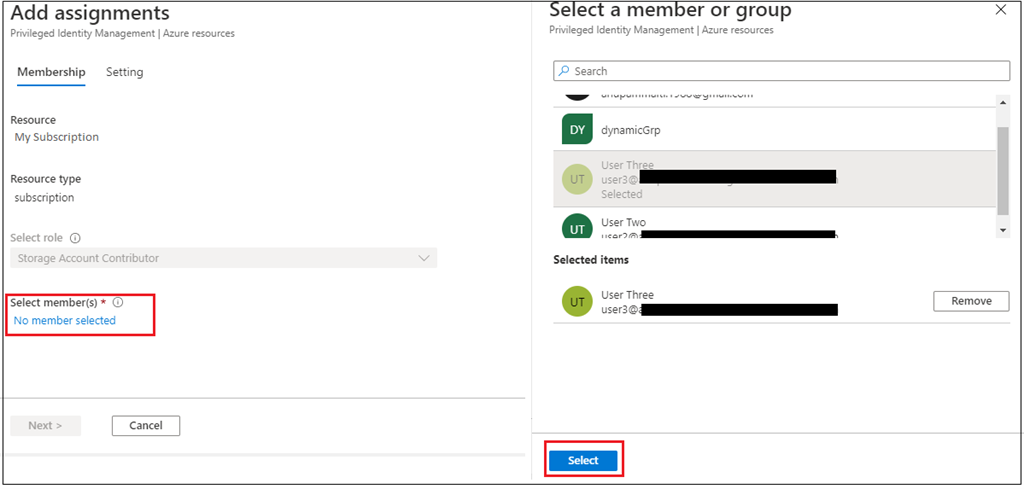
Now within the settings tab, you’ve got completely different settings in place.
If you wish to assign the function immediately onto the consumer, then select the project kind as Energetic.
If you wish to make sure that a consumer is eligible to take up a task, then you’ll be able to select the project kind as Eligible. On this case, customers must Activate the function.
Right here, I’m choosing the project kind as Eligible.
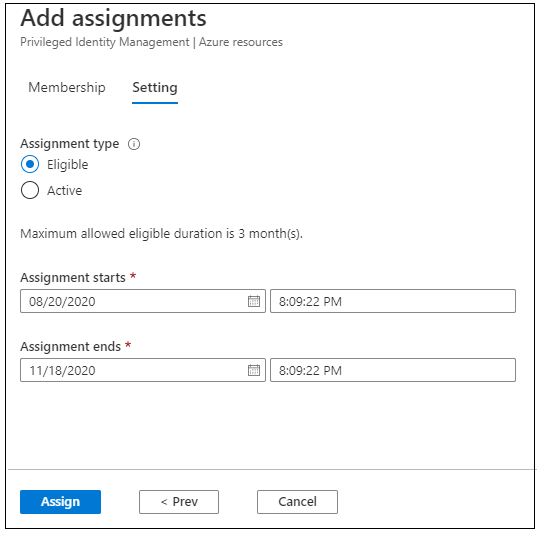
Please guarantee that the distinction between Task begins thus far and the Task ends mustn’t exceed greater than three months. It’s because we modified Storage Account Contributor function settings in earlier steps.
After assigning the function to the consumer, we will see the related membership standing for the consumer underneath “Eligible assignments”.
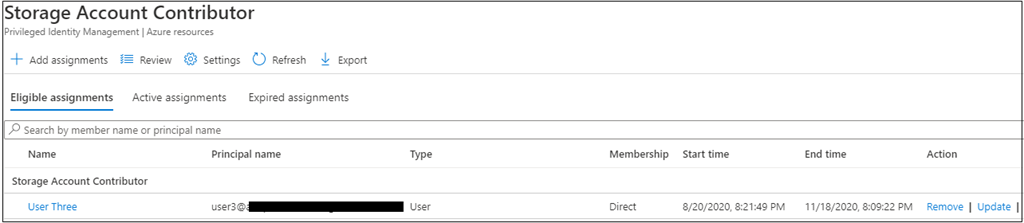
To this point we’ve got modified RBAC function settings and assigned that function to a consumer as eligible. So as to get entry, customers must activate the function.
Activate function from Privileged Person
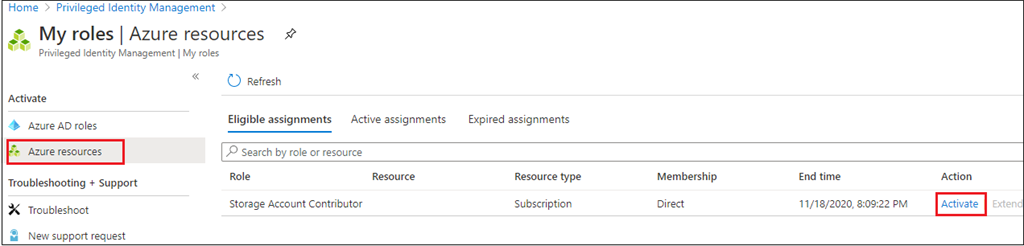
Now go forward and log in to the Azure portal along with your privileged consumer (in my case Person Three) and activate the function.
When you navigate to Privileged Id Administration and click on on My roles => Click on on Azure assets => Activate.
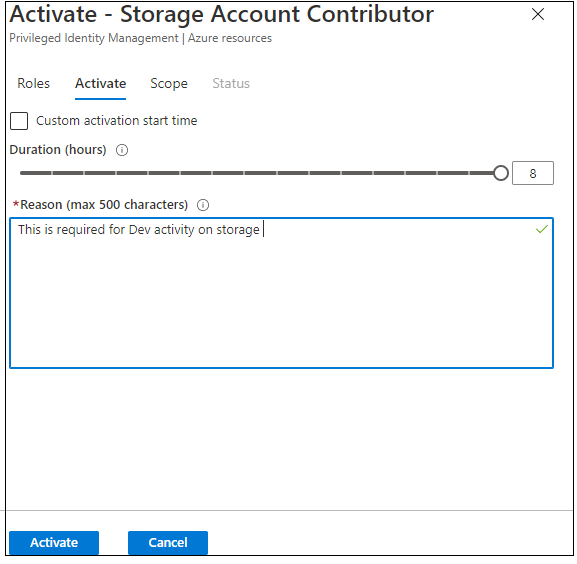
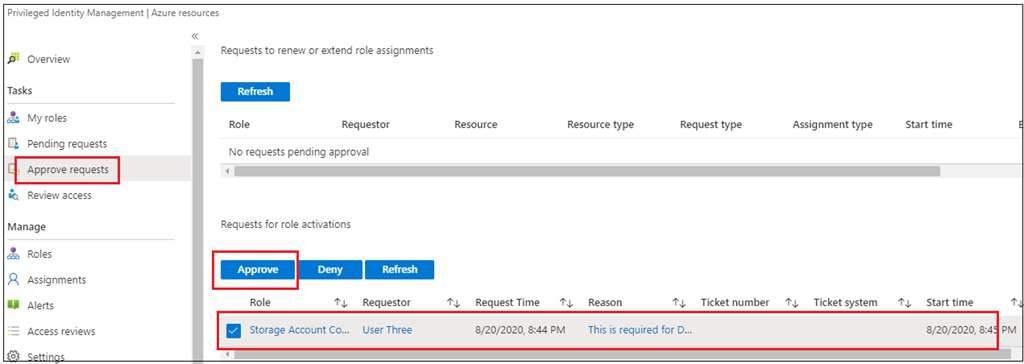
Approve Entry Request from International Administrator
Now the worldwide administrator can approve the request from the approve request tab.
Now the privileged consumer has efficiently assigned the Storage Account Contributor function.
Keep in mind that as soon as the function is expired after eight hours (as per settings), then the consumer can once more go forward and activate the function. However keep in mind the function can solely be activated between that begin and finish date.
Wonderful! We’ve seen an illustration of methods to assign time-bound entry to assets utilizing begin and finish dates in Azure AD PIM. Additionally, we’ve got ensured that approval is required to activate any of those privileged roles.
I hope you discover this info helpful!