Assigning A Constructed-in Position To A Person At Useful resource And Useful resource Group Scope Utilizing ARM Template
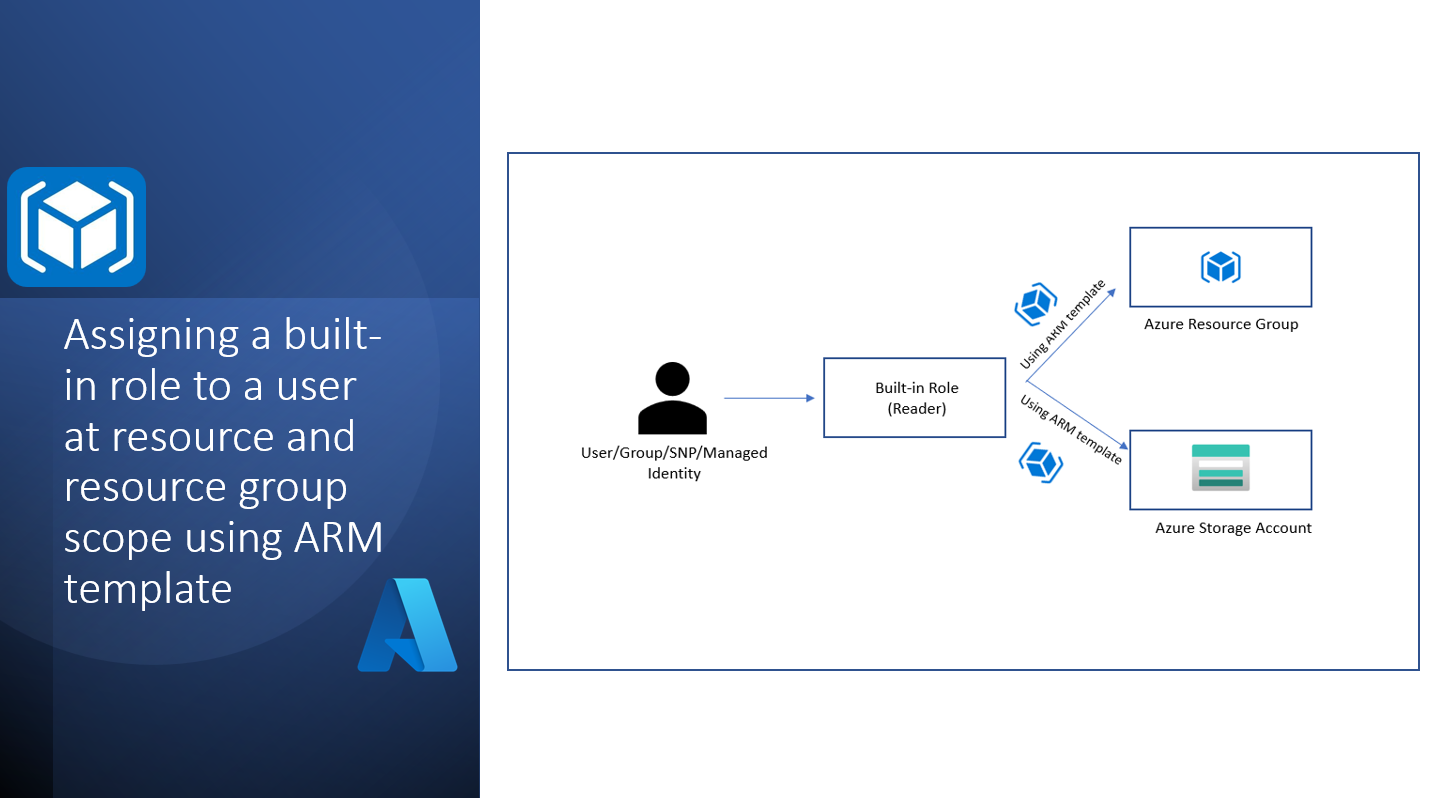
This text is concentrated on creating an ARM template that may create a storage account useful resource within the useful resource group and can assign position at each RG (Useful resource Group) scope and created storage account useful resource degree
This text is split into following 5 sections, As it’s described within the picture proven beneath
- Fetch Person Object ID
- Fetch Constructed-in Position ID
- Create ARM template to provision storage account
- Position task in ARM template
- Deploying ARM template to Azure Portal
Let’s begin step-by-step as talked about above, we are going to fetch the person object ID which will likely be utilized in deploying ARM template
- So firstly, let’s fetch the person’s object id
Use the PowerShell script to fetch person’s object id by its e mail id.
Get-AzADUser | The place-Object { $_.UserPrincipalName -eq “testuser@testdomain.xyz.com” }
It will present the person particulars like, DisplayName, Id, Mail, UserPrincipalName, Seize the Id and reserve it for additional use
You can even fetch the person object Id from Azure Portal, Navigate to Azure Lively Director > Customers > Choose the person you need to fetch the Id of > Copy the Object Id
- Equally, we are going to fetch the built-in position Id utilizing PowerShell script, for this text I’ll fetch the “Reader” position id however you’ll be able to fetch your required position id,
Get-AzRoleDefinition -Identify Reader
This script will output few of the Position particulars, seize the Id from the output and reserve it for additional use
- Now it’s time to create the ARM Template which is able to create the Storage account and assign person with Reader position to the created storage account additionally, we are going to assign person with Reader position to the Useful resource group utilizing scope.
Comply with the template talked about beneath for creating storage account and position task.
Refer Microsoft documentation to know extra on ARM Template syntax and particulars and to know extra particulars on position task
{
"$schema": "https://schema.administration.azure.com/schemas/2015-01-01/deploymentTemplate.json#",
"contentVersion": "1.0.0.0",
"parameters": {
"AAD_Object_ID": {
"metadata": {
"description": "Object ID of the Person, Group or Service Principal"
},
"sort": "string"
},
"Role_Definition_ID": {
"metadata": {
"description": "Identifier (GUID) of the position definition to map to service principal"
},
"sort": "string"
}
},
"variables": {
"Full Role_Definition_ID": "[concat('/subscriptions/', subscription().subscriptionId, '/providers/Microsoft.Authorization/roleDefinitions/', parameters('Role_Definition_ID'))]",
"StorageAccountName": "shrstrgacc",
"StorageAccountAssignmentName": "[concat(variables('StorageAccountName'), '/Microsoft.Authorization/', guid(concat(resourceGroup().id), variables('Full Role_Definition_ID')))]"
},
"assets": [
{
"type": "Microsoft.Storage/storageAccounts",
"apiVersion": "2018-07-01",
"name": "[variables('StorageAccountName')]",
"feedback": "Storage account used to retailer VM disks",
"location": "[resourceGroup().location]",
"sku": {
"title": "Standard_LRS"
},
"sort": "Storage",
"properties": {
"roleDefinitionId": "[variables('Full Role_Definition_ID')]",
"principalId": "[parameters('AAD_Object_ID')]"
}
},
{
"sort": "Microsoft.Authorization/roleAssignments",
"apiVersion": "2017-09-01",
"title": "[guid(concat(resourceGroup().id), resourceId('Microsoft.Storage/storageAccounts', 'shrstrgacc'), variables('Full Role_Definition_ID'))]",
"dependsOn": [
"[resourceId('Microsoft.Storage/storageAccounts', 'shrstrgacc')]"
],
"properties": {
"roleDefinitionId": "[variables('Full Role_Definition_ID')]",
"principalId": "[parameters('AAD_Object_ID')]",
"scope": "[resourceGroup().id]"
}
},
{
"sort": "Microsoft.Storage/storageAccounts/suppliers/roleAssignments",
"apiVersion": "2017-05-01",
"title": "[variables('StorageAccountAssignmentName')]",
"dependsOn": [
"[resourceId('Microsoft.Storage/storageAccounts', 'shrstrgacc')]"
],
"properties": {
"roleDefinitionId": "[variables('Full Role_Definition_ID')]",
"principalId": "[parameters('AAD_Object_ID')]"
}
}
],
"outputs": {}
}
As you’ll be able to see from the above ARM template, we now have given 2 enter parameters that are, “AAD_Object_ID” & “Role_Definition_ID”, so to offer a short about what this enter parameter will maintain, AAD_Object_ID would be the Person object Id fetched from Step 1 and Role_Definitation_ID would be the inbuilt Reader Position ID fetched from Step 2
To additional drill right down to the ARM Template assets, we will likely be utilizing
Kind: Microsoft.Storage/storageAccounts to provision storage account with the talked about properties within the ARM Template
Kind: Microsoft.Authorization/roleAssignments to assign position at Useful resource group scope
Kind: Microsoft.Storage/storageAccounts/suppliers/roleAssignments to assign position to the storage account useful resource
Additionally, save the above talked about template code in a file with .json extension for instance armtest.json and replica the file path as we are going to want it whereas deploying it to Azure within the last step
Now it’s the time to deploy ARM Template to Azure Portal use the next script
Connect with Azure Account
Join Az-Account
# Use PowerShell command New-AzResourceGroupDeployment, this command deploys azure assets to the Useful resource group
Refer, Microsoft documentation on deploying utilizing New-AzResourceGroupDeployment
New-AzResourceGroupDeployment -ResourceGroupName <your- resource-group-name>`
-TemplateFile <ARMTemplateFilePath > `
-AAD_Object_ID <person object Id> `
-Role_Definition_ID <Inbuilt Reader position Id>
Word – Cross the copied path of the saved ARM Template file to the TemplateFile parameter within the script
Now it’s time to confirm the end result within the Azure Portal,
Wohoo, Storage is created within the Useful resource group talked about within the New- AzResourceGroupDeployment
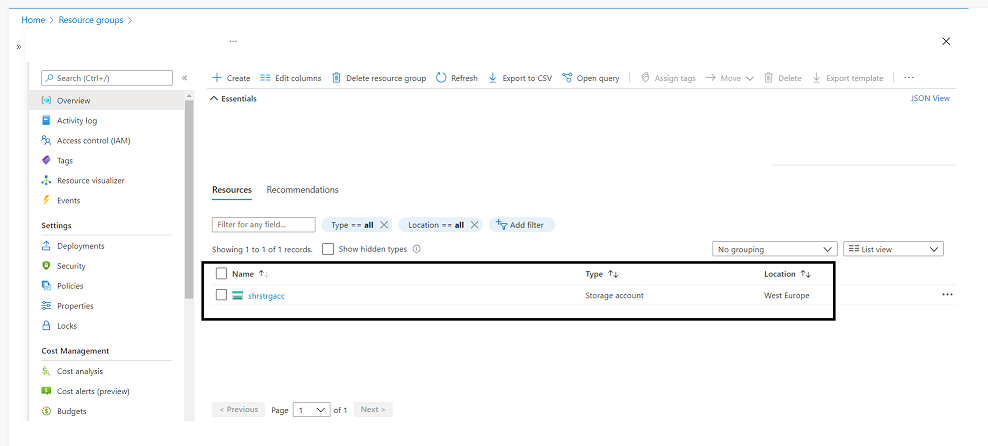
Fig 1.1: Storage Account created utilizing ARM Template
Now, Let’s test if the Reader position to the testuser is assigned to the Useful resource Group
Navigate to Azure Portal > Useful resource Group > Choose the Useful resource group you added within the ARM deployment script > Entry Management > Position Assignments
Woohoo, we will see the Reader position to the take a look at person is assigned entry to the Useful resource Group scope
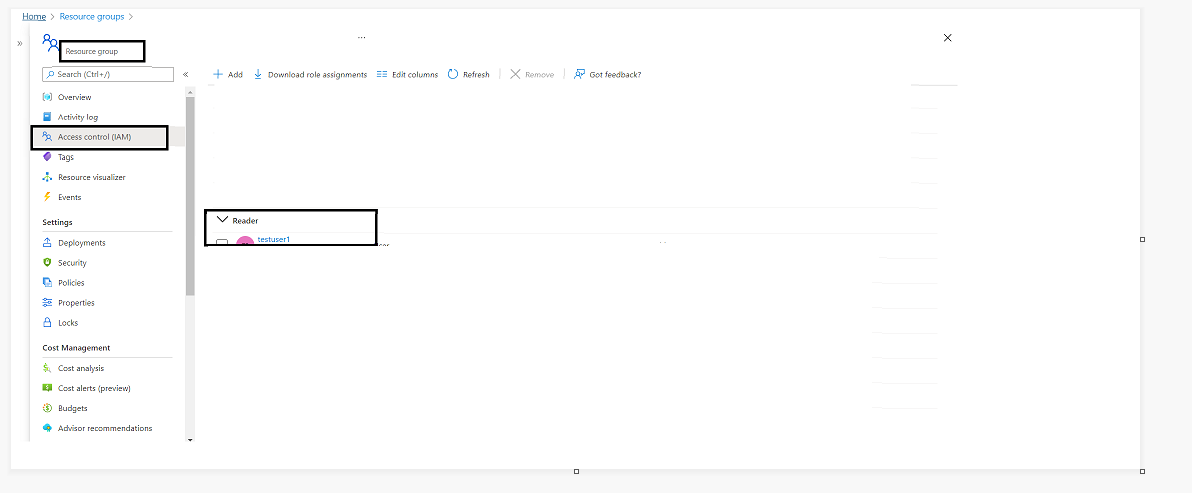
Fig 1.2: Position Task to the Useful resource Group
It’s time to confirm the position entry on the storage account useful resource degree,
Navigate to Azure Portal > Useful resource Group > Choose the Useful resource group you added within the ARM deployment script > Choose the created storage account > Entry management > Position Assignments
Wohoo, at storage account degree we will see the reader position is assigned to the take a look at person and the identical is inherited from the Useful resource Group.
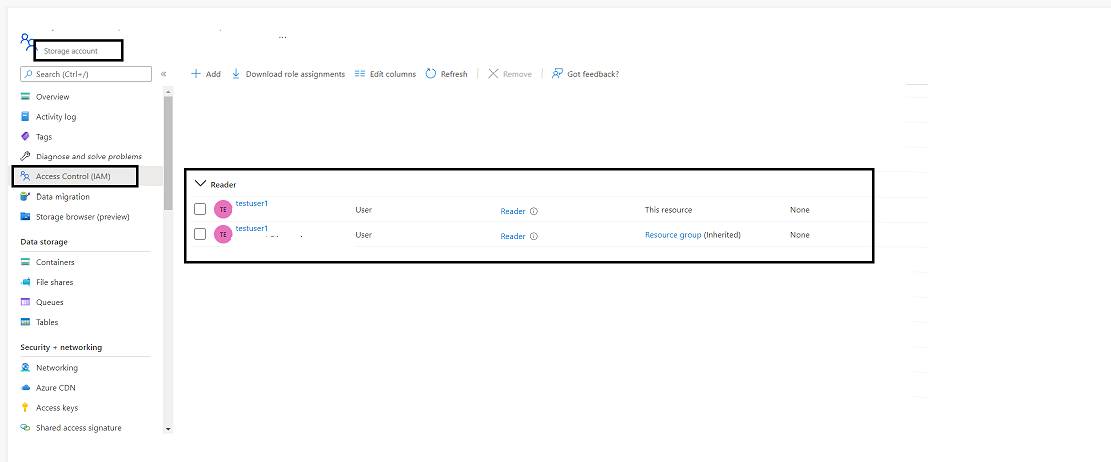
Fig 1.3: Position assigned to created storage account utilizing ARM Template
I hope this text appears helpful for all of the Azure fanatics on how they will assign RBAC to the customers/teams/SPNs/Managed Identities utilizing ARM Template.
Preserve Studying!
Preserve Sharing!